A Network Vulnerability Assessment Report Sample is a crucial tool for identifying and addressing vulnerabilities in your network. Learn all about it in this comprehensive guide.
Network security is a critical concern for any organization, big or small. With cyber threats increasing every day, it’s more important than ever to ensure that your network is secure. A network vulnerability assessment is a comprehensive evaluation of your network’s security posture. The assessment helps identify vulnerabilities, weaknesses, and gaps in your network security. A Network Vulnerability Assessment Report Sample is a crucial tool for identifying and addressing vulnerabilities in your network. In this article, we will explore everything you need to know about the Network Vulnerability Assessment Report Sample.
What is a Network Vulnerability Assessment Report Sample?
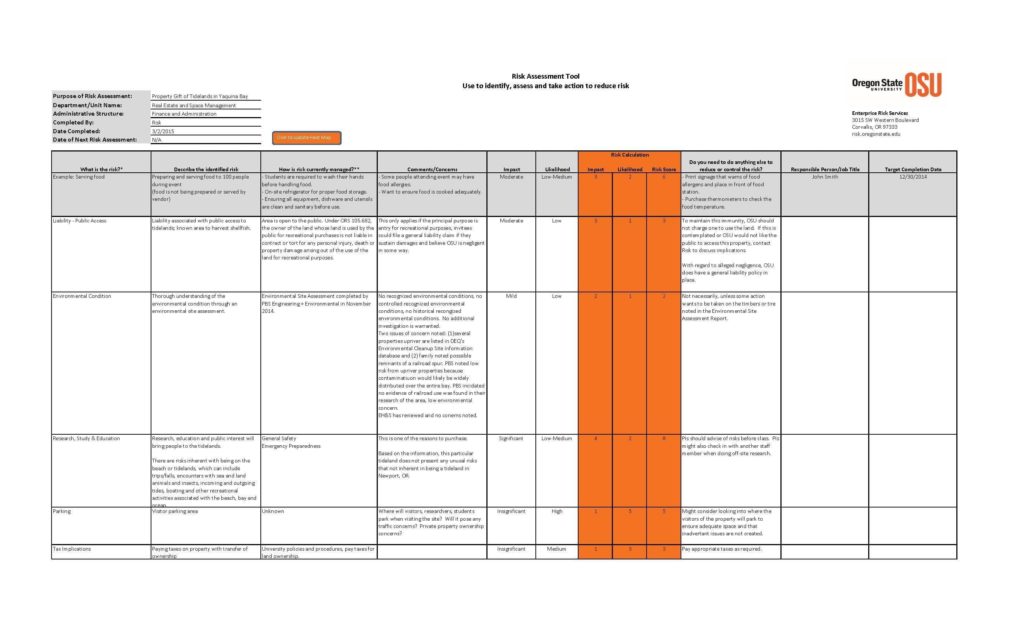
A Network Vulnerability Assessment Report Sample is a document that presents the results of a network vulnerability assessment. It provides a detailed analysis of the vulnerabilities discovered in the network, their impact, and recommendations for remediation. The report sample includes a summary of the assessment methodology, findings, and recommendations.
Why is a Network Vulnerability Assessment Report Sample important?
A Network Vulnerability Assessment Report Sample is essential for several reasons. Firstly, it provides a comprehensive overview of the security posture of your network. It helps identify potential threats and vulnerabilities that can be exploited by attackers. Secondly, it helps prioritize remediation efforts. The report sample lists vulnerabilities based on their severity and the impact they could have on your organization. This helps prioritize remediation efforts, ensuring that the most critical vulnerabilities are addressed first. Finally, the report sample provides recommendations for remediation. The recommendations are based on industry best practices and are tailored to your organization’s specific needs.
What does a Network Vulnerability Assessment Report Sample include?
A Network Vulnerability Assessment Report Sample includes several key elements. These elements include:
- Executive Summary
A summary of the assessment methodology, findings, and recommendations. - Scope
The scope of the assessment, including the systems, devices, and applications assessed. - Methodology
The assessment methodology used to identify vulnerabilities. - Findings
A detailed analysis of the vulnerabilities discovered, their impact, and severity. - Recommendations
Recommendations for remediation, based on industry best practices and tailored to your organization’s needs. - Conclusion
A summary of the assessment findings and recommendations.
How is a Network Vulnerability Assessment Report Sample generated?
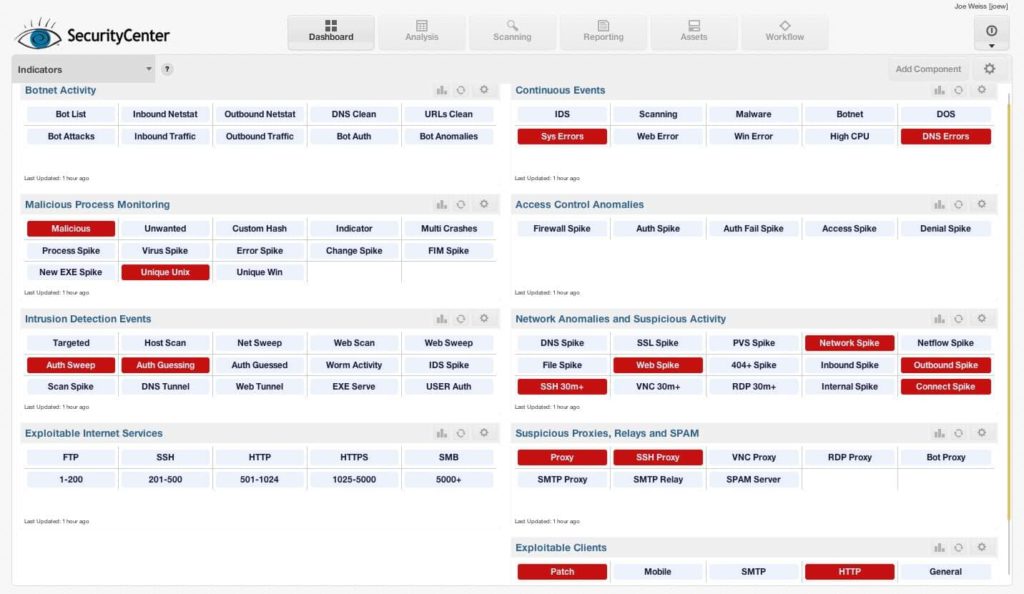
A Network Vulnerability Assessment Report Sample is generated using automated tools that scan your network for vulnerabilities. These tools use various methods to identify vulnerabilities, including port scanning, vulnerability scanning, and penetration testing. Once the vulnerabilities are identified, the report sample is generated, and the findings are analyzed. The report sample is then reviewed by security experts who provide additional insights and recommendations.
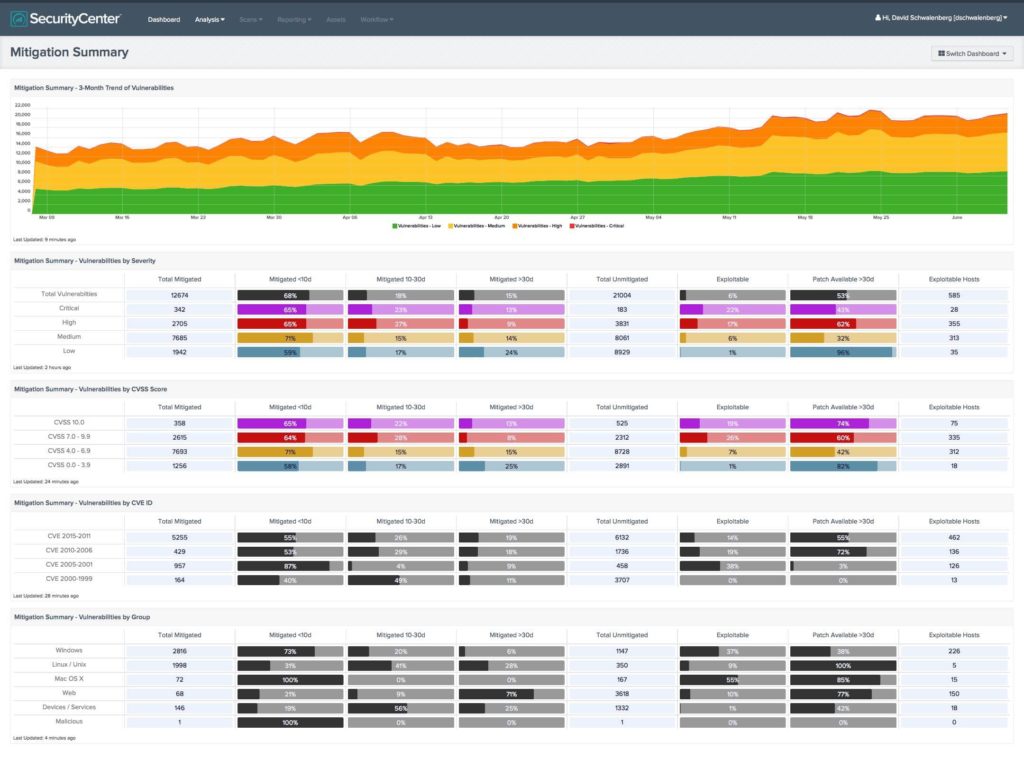
Regular vulnerability assessments and generating Network Vulnerability Assessment Report Samples can help identify and address vulnerabilities before they can be exploited by attackers. This can help prevent data breaches and protect your organization’s sensitive information. In addition, regular vulnerability assessments can help you comply with industry regulations and standards such as PCI DSS, HIPAA, and GDPR.
It’s important to note that a Network Vulnerability Assessment Report Sample is not a one-time solution. It’s a continuous process that requires regular assessments and updates. As new threats emerge, your network’s security posture may change, and new vulnerabilities may be discovered. Regular assessments and report samples can help you stay on top of these changes and ensure that your network remains secure.
Conclusion
A Network Vulnerability Assessment Report Sample is a crucial tool for identifying and addressing vulnerabilities in your network. It provides a comprehensive overview of the security posture of your network and helps prioritize remediation efforts. The report sample includes recommendations for remediation based on industry best practices and tailored to your organization’s specific needs. A Network Vulnerability Assessment Report Sample is generated using automated tools that scan your network for vulnerabilities. To ensure the security of your network, it’s important to conduct regular vulnerability assessments and generate Network Vulnerability Assessment Report Samples.