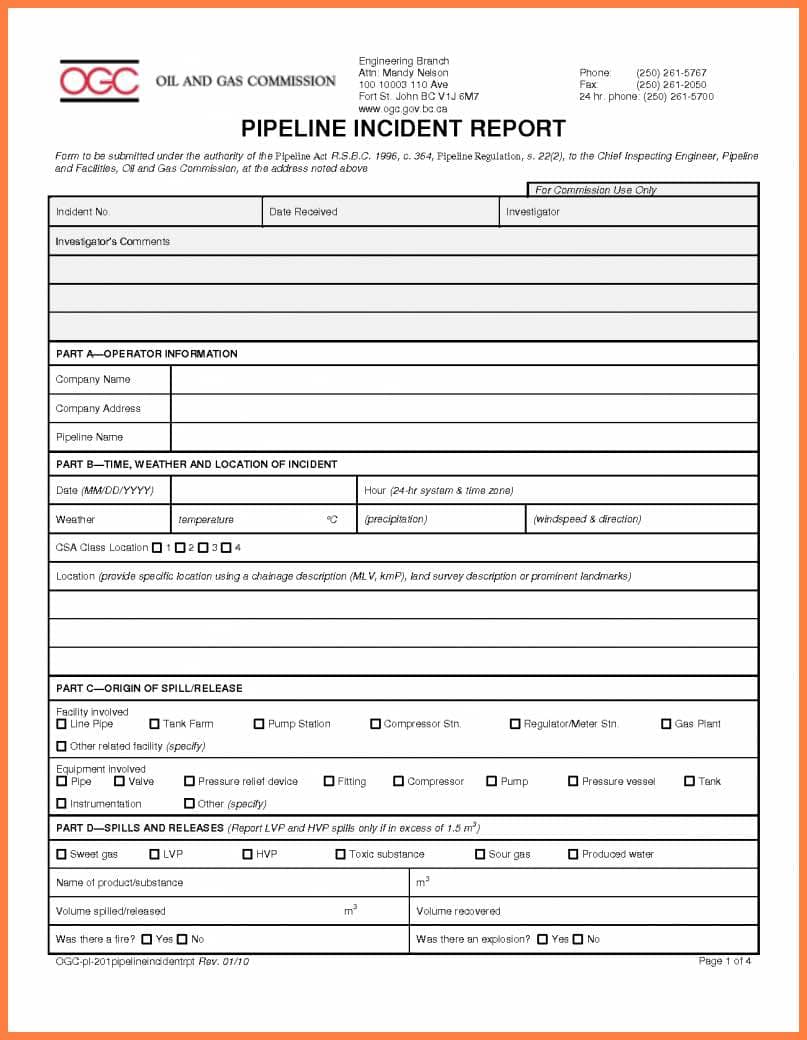
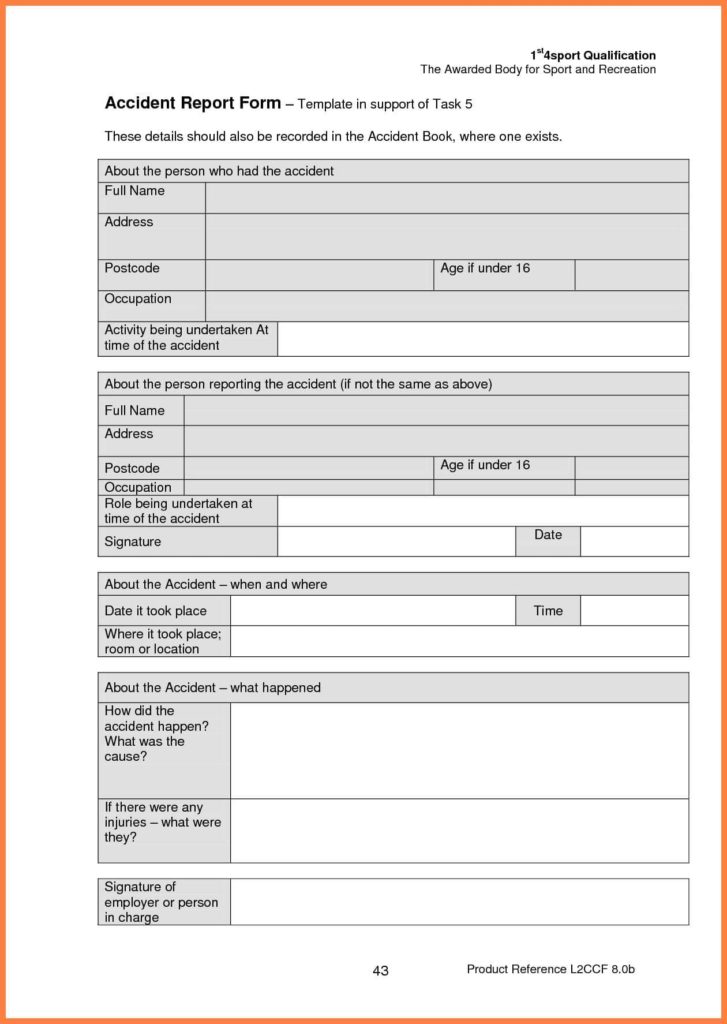
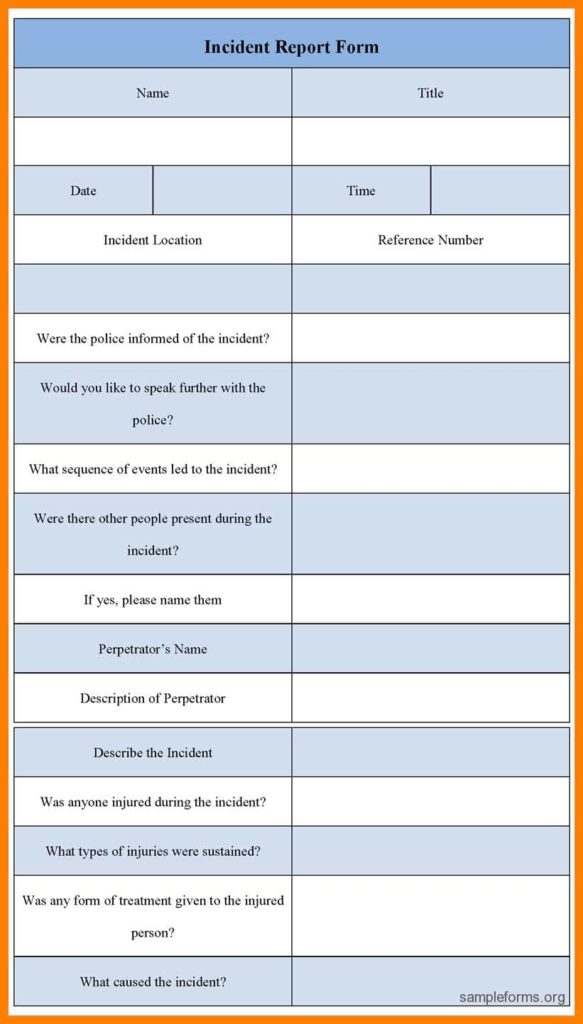
This article will cover a quick introduction to the Security Incident Report Form. After this article is complete, I’ll provide more detailed information on each of the seven sections of the form and provide examples. At the end of this introduction, you should be able to implement this form in your company.
First, I need to discuss why a security incident report form is needed. Today’s IT world is highly sophisticated and, as a result, the way people deal with it can become a serious security issue. The security industry has come a long way since the days of firewalls and intrusion detection systems. It has become much more difficult to defend against a wide range of threats. This trend continues as more users start using computers and cell phones.
Since the industry is expanding so rapidly, many businesses are finding themselves in critical points of failure in the coming years. A lack of information sharing is one of the most critical points. A breach of security leads to the potential loss of customer data and business assets.

To protect against these critical points, a system must be established that effectively shares the information about a wide range of threats. Businesses will look to a Security Incident Report Form to help them make important decisions. It is the process of collecting, collating, and sorting information that is so critical for the success of a security system.
The Security Incident Report Form can also help you make sense of events that happen when a particular system is not operational. These events can include scheduled maintenance or unexpected problems. In the event of an emergency situation, they can help provide necessary information about the location of the system, the status of the network, and the root cause of the problem. In these situations, the system must be inspected and configured in a way that prevents future occurrences of the event.
They also provide the ability to highlight errors messages. This enables you to understand exactly what the system was experiencing. Once the problem is identified, it becomes easier to control the system and begin to implement a plan to resolve the problem.
Finally, the system can be used to monitor the business environment. For example, if an employee is performing work that is taking up a large portion of the office’s time, he/she can be monitored remotely via email or mobile device. You could also monitor the system at home or at the office. This way, you can ensure that all necessary items are being properly serviced at the correct time.
I hope this brief introduction to the Security Incident Report Form has provided you with the information you need to get started. Please feel free to check out our website for more detailed information on this matter.