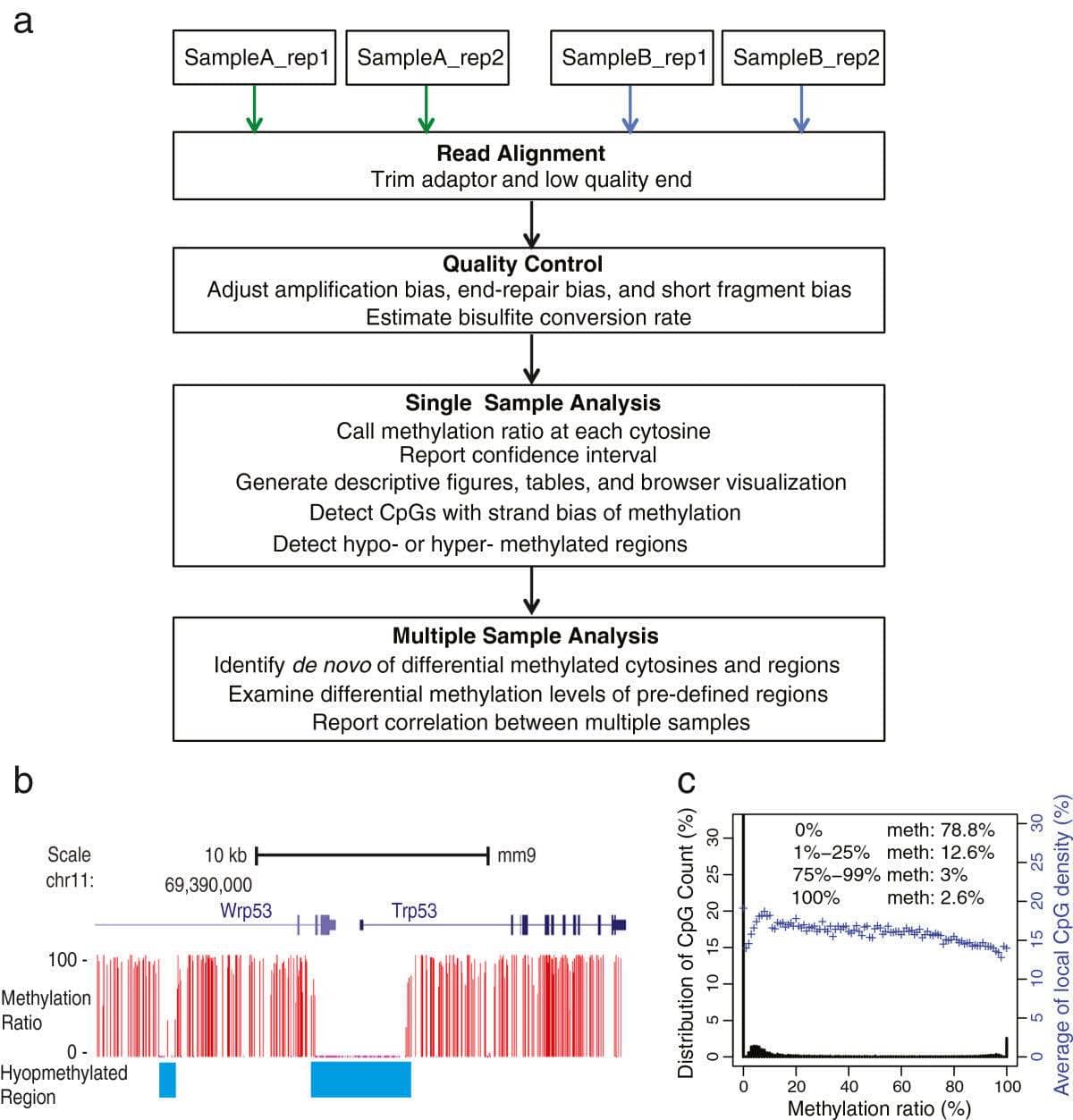
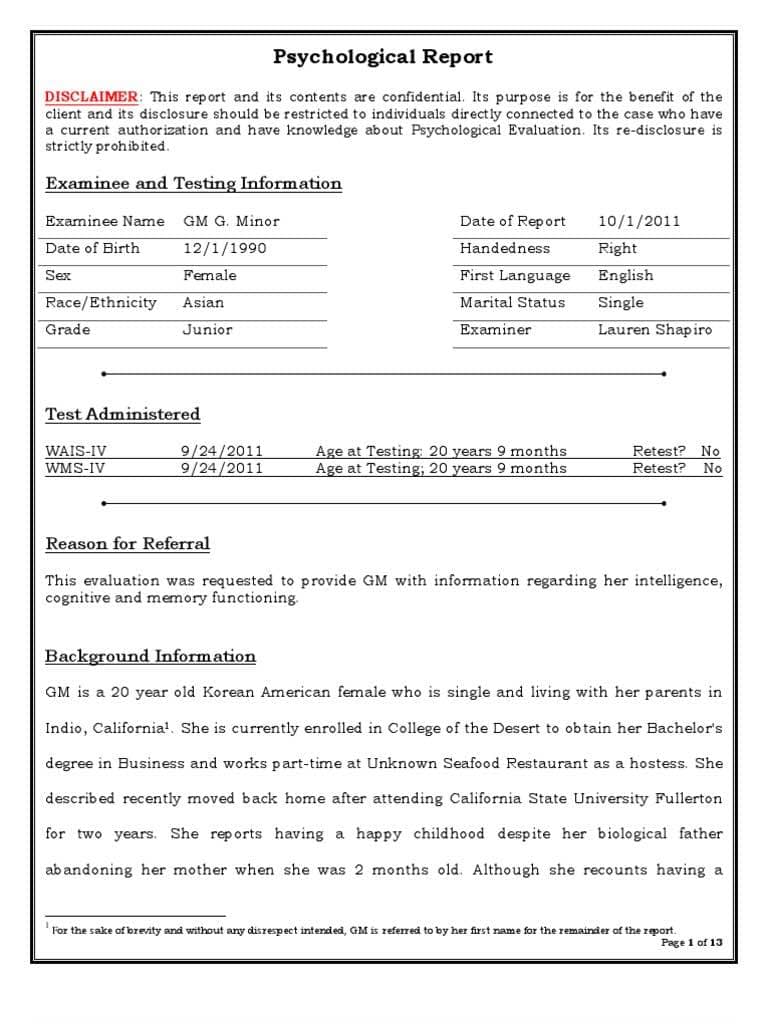
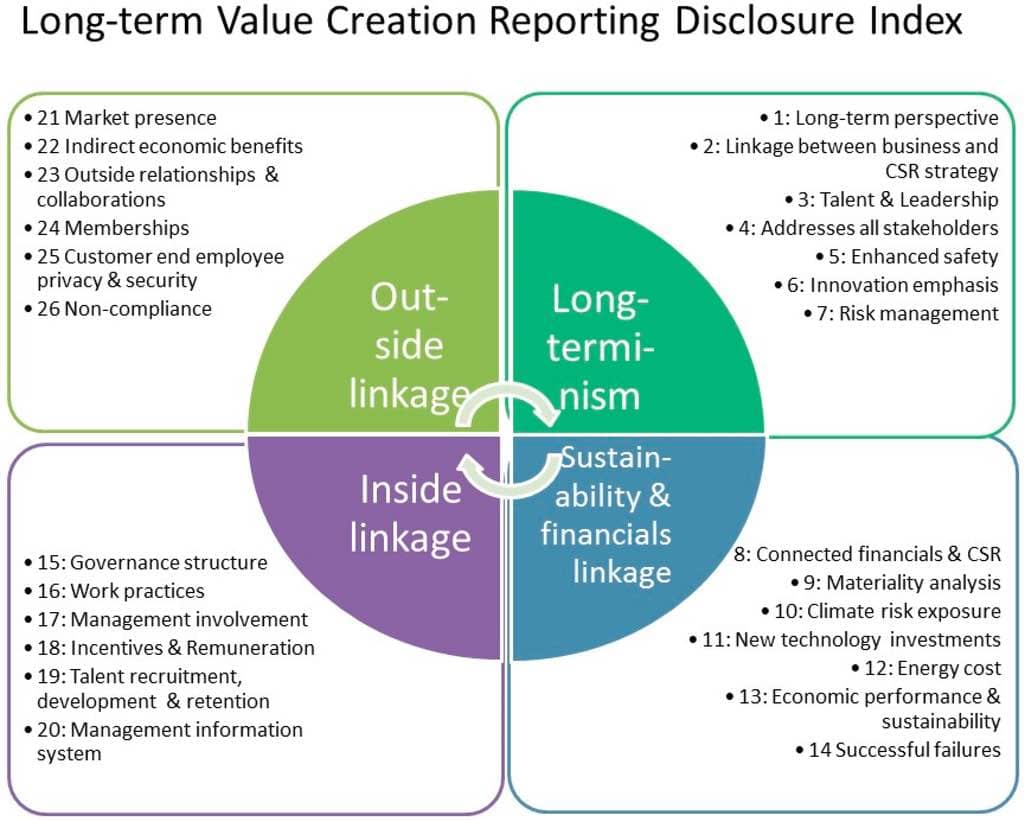
Discover the significance of a Sample SOC 1 Report and how it can benefit your organization. Dive into this informative guide to understand its importance, components, and how to create one.
In the fast-paced world of business, security and compliance are paramount. One of the essential tools to evaluate the effectiveness of a service organization’s internal controls is a Sample SOC 1 Report. This comprehensive guide aims to demystify the significance, components, and creation of a Sample SOC 1 Report, providing you with valuable insights for your organization’s success.
Understanding a Sample SOC 1 Report
A Sample SOC 1 Report, or System and Organization Controls 1 Report, is a critical document that service organizations provide to their clients and stakeholders. It is designed to provide assurance that the organization’s internal controls are reliable and functioning effectively. But what does this report entail, and why is it so crucial?
A Sample SOC 1 Report primarily focuses on the evaluation of internal controls relevant to financial reporting. It assesses the service organization’s ability to process transactions accurately and maintain data integrity, which, in turn, impacts the financial statements of the organization’s clients. In essence, this report offers an independent and expert opinion on the controls that affect financial reporting.
Components of a Sample SOC 1 Report
- Management’s Assertion
The report begins with management’s assertion, where the service organization’s management formally states its responsibility for the system and its control environment. - Description of the System
This section provides a detailed overview of the service organization’s system, including its operational and control activities. - Control Objectives
The report outlines the control objectives that the system aims to achieve, ensuring that they are aligned with the client’s financial reporting needs. - Control Activities
This is a critical part of the report that delves into the specific control activities implemented by the service organization. It details the design and operating effectiveness of these controls. - Test Procedures and Results
The report includes information on the testing procedures performed to evaluate the controls’ effectiveness. It offers insights into the testing methodology, results, and any identified deficiencies. - Opinion
The independent auditor provides an opinion on the suitability and operating effectiveness of the controls. This opinion is crucial for clients and stakeholders in assessing the organization’s trustworthiness.
Importance of a Sample SOC 1 Report
- Builds Trust
A Sample SOC 1 Report fosters trust among clients and stakeholders by demonstrating the organization’s commitment to effective internal controls. - Meets Regulatory Requirements
Many regulatory bodies require service organizations to provide SOC 1 reports to ensure compliance with industry standards and best practices. - Competitive Advantage
Having a favorable SOC 1 report can give your organization a competitive edge in the marketplace, as it signifies your dedication to security and compliance. - Safeguards Client Interests
Clients rely on SOC 1 reports to evaluate the security and reliability of their service providers, ensuring the protection of their financial data.
Creating a Sample SOC 1 Report
- Engage a Qualified Service Auditor
The first step in creating a Sample SOC 1 Report is to engage a qualified service auditor. They will assess your controls, test them, and provide an objective opinion. - Prepare a Description of the System
Collaborate with the auditor to prepare a comprehensive description of your organization’s system and control activities. - Define Control Objectives
Clearly define the control objectives that your organization aims to achieve, ensuring they are aligned with your client’s needs. - Implement Control Activities
Develop and implement control activities that are designed to meet the defined control objectives. - Testing and Audit
The auditor will conduct testing procedures to evaluate the controls’ effectiveness. Any deficiencies identified should be addressed promptly. - Auditor’s Report
Once the audit is completed, the auditor will issue a report providing their opinion on the controls.
In conclusion, a Sample SOC 1 Report is a valuable asset for service organizations, offering assurance to clients and stakeholders regarding the effectiveness of their internal controls. By understanding its components and importance, as well as following the steps to create one, your organization can navigate the complex landscape of compliance, build trust, and gain a competitive advantage in today’s business world. So, don’t overlook the power of a well-prepared Sample SOC 1 Report – it’s your key to success in a secure and compliant business environment.