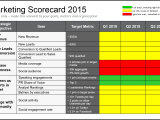
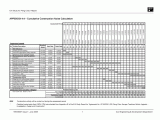
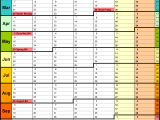
A Sample Security Audit Report is used by security professionals to determine what the most likely risk is. This report provides an overview of the vulnerabilities that exist within a system and helps to identify areas that require further investigation. In many cases, the report identifies areas that may need more focus on.
When performing a Security Audit, a sample of this type is provided to a potential customer to allow them to get a better feel for the overall process. The document is also used as a standard of comparison. When a company is doing a Security Audit, there are many things to consider. There are also many levels of risk. Here is a short discussion of the different types of risks and how they may affect the audit.
The first category is considered a high risk or an extremely complicated system. Systems such as computer networks, air-conditioning systems, and medical equipment are considered to be systems with high risk factors. While these systems may have been designed very well and may not pose a threat, they are very complex. For instance, a network can consist of hundreds or even thousands of computers. All these computers may be connected to the network by one or more network cables.
Many times, when a computer is infected, the virus will find itself attached to the network cable, making it easy for someone to get in and out. Even the smallest amount of time spent in an infected computer could bring about the infection spreading from computer to computer. Because of this, there are usually many things to consider when performing a Security Audit.
Most high-risk systems also have a backup and recovery plan in place. However, this plan is often not complete and often does not contain all of the information needed to recover data if the system does break down or stop operating properly. This is why the use of a Sample Security Audit report is so important.
High-risk systems that are considered less complicated typically do not have backup and recovery plans at all. Some systems only include a physical inventory system, such as a computer that contains its own hard drive. The physical inventory system may include a list of the software programs installed but does not include any information on the software itself. This may allow anyone to change the settings and software files that are in place without notice.

A system that has backup and recovery plans will contain all of the information required to restore the system to its proper operating condition. It will also contain the operating system, hardware configuration, and other types of configurations. These reports can help the owner to determine if the system is ready to run again.
Once you determine the level of risk a system has, you should make sure that the system is as secure as possible. A good example of this would be using a sample report to test the security of a fire alarm system, which contains an audit of the system’s physical hardware and software. If a fire does occur, the high-risk assessment will ensure that it will not pose a threat to the building.
If your system is a networked computer, then you should perform an audit of the network. It should contain an analysis of the network’s security and configuration. The analysis should also include information on the passwords used to access the network.
In order to learn how to properly complete a Sample Security Audit Report, it will help to look at other samples as well. A good example would be a report that provides information on how to handle the detection of data loss and what should be done when the loss is detected. This report will also provide information on whether or not the business network is password protected or not.
While most companies do not require that their systems have a Sample Security Audit report, it is always good practice to review it before an actual audit is conducted. You never know when something that is found will become problematic or cause a problem for your company. It is always good to be prepared for the worst case scenario.