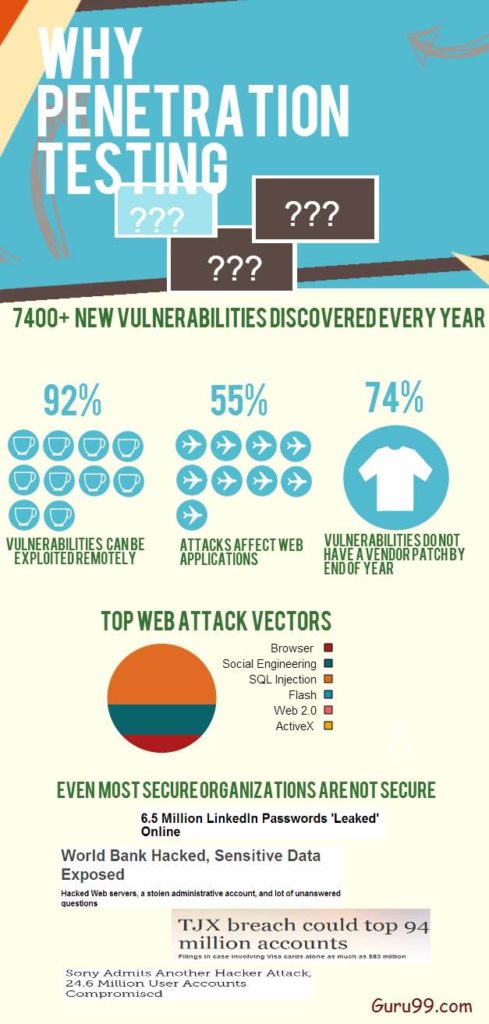
Dive into the world of Penetration Testing Report Samples and discover the importance of this essential cybersecurity tool. Explore the key components and best practices in this comprehensive guide.
In today’s digital age, where information is the lifeblood of businesses and organizations, cybersecurity has become more critical than ever. As cyber threats continue to evolve, the need for robust defenses against potential breaches is paramount. One vital aspect of this defense is penetration testing, and the cornerstone of a successful penetration test is the Penetration Testing Report Sample.
What is a Penetration Testing Report Sample?
A Penetration Testing Report Sample is a detailed document that provides a comprehensive analysis of the security posture of an organization. It is the culmination of a penetration test, which is a simulated cyberattack on an organization’s systems, networks, and applications. The report serves as a valuable resource for organizations to understand their vulnerabilities and take necessary actions to bolster their cybersecurity defenses.
Key Components of a Penetration Testing Report Sample
- Executive Summary
This section provides a high-level overview of the test, its objectives, and the main findings. It’s typically written in non-technical language, making it accessible to stakeholders who may not have a deep understanding of cybersecurity. - Scope and Methodology
This part outlines the scope of the test, including the systems, networks, and applications examined. It also describes the testing methods, tools, and techniques used during the assessment. - Findings and Vulnerabilities
The heart of the report, this section details the vulnerabilities and weaknesses discovered during the penetration test. Each issue is described, categorized by severity, and accompanied by recommendations for remediation. - Evidence and Documentation
To support their findings, penetration testers include evidence such as screenshots, logs, and technical data. This ensures that the identified vulnerabilities are well-documented and can be easily validated. - Risk Assessment
An evaluation of the potential impact of each vulnerability is provided, along with a risk rating. This helps organizations prioritize their remediation efforts based on the level of risk associated with each issue. - Recommendations
A set of actionable recommendations is included to guide the organization in addressing the identified vulnerabilities. These suggestions are designed to improve security and prevent future breaches. - Appendices
Additional information, such as testing scripts, technical details, and supplementary documentation, may be included in the appendices for reference.
Why is a Penetration Testing Report Sample Important?
A Penetration Testing Report Sample is a critical tool for several reasons:
- Identification of Vulnerabilities
It reveals the security weaknesses and vulnerabilities within an organization, enabling proactive measures to be taken to mitigate them. - Compliance
Many industries and regulations require regular penetration testing and the submission of reports to ensure data protection and cybersecurity compliance. - Risk Mitigation
The report helps organizations prioritize and address vulnerabilities based on their potential impact, reducing the risk of security breaches. - Continuous Improvement
Penetration testing and the subsequent reports are part of an ongoing process that allows organizations to continuously enhance their security posture.
Best Practices for Creating a Penetration Testing Report Sample
To ensure the effectiveness of a Penetration Testing Report Sample, consider the following best practices:
- Clarity and Transparency
Use clear and concise language to explain findings and recommendations. Ensure that all stakeholders can understand the report’s content. - Actionable Recommendations
Provide specific, actionable steps for addressing vulnerabilities, making it easier for organizations to take corrective action. - Prioritization
Categorize vulnerabilities based on their severity and potential impact, enabling organizations to focus on the most critical issues first. - Visual Aids
Incorporate visual aids like charts and graphs to enhance the report’s readability and comprehension. - Regular Updates
Regularly conduct penetration tests and update the report to reflect the current security posture and evolving threats.
In conclusion, a Penetration Testing Report Sample is a crucial asset in the realm of cybersecurity. It not only uncovers vulnerabilities but also equips organizations with the knowledge and guidance needed to fortify their defenses. By following best practices and utilizing these reports effectively, businesses and institutions can safeguard their digital assets and maintain the trust of their stakeholders in an increasingly interconnected world.