Learn what SOC Report Example is, why it’s important, and what types of SOC reports are available. Get examples of SOC reports to help you understand how they work.
As a business owner, you want to ensure that your customers and clients trust you with their sensitive information. One way to demonstrate your commitment to data security is by obtaining a SOC Report Example. In this article, we’ll explain what SOC Report Example is and why it’s important, as well as provide examples of the different types of SOC reports available.
What is a SOC Report Example?
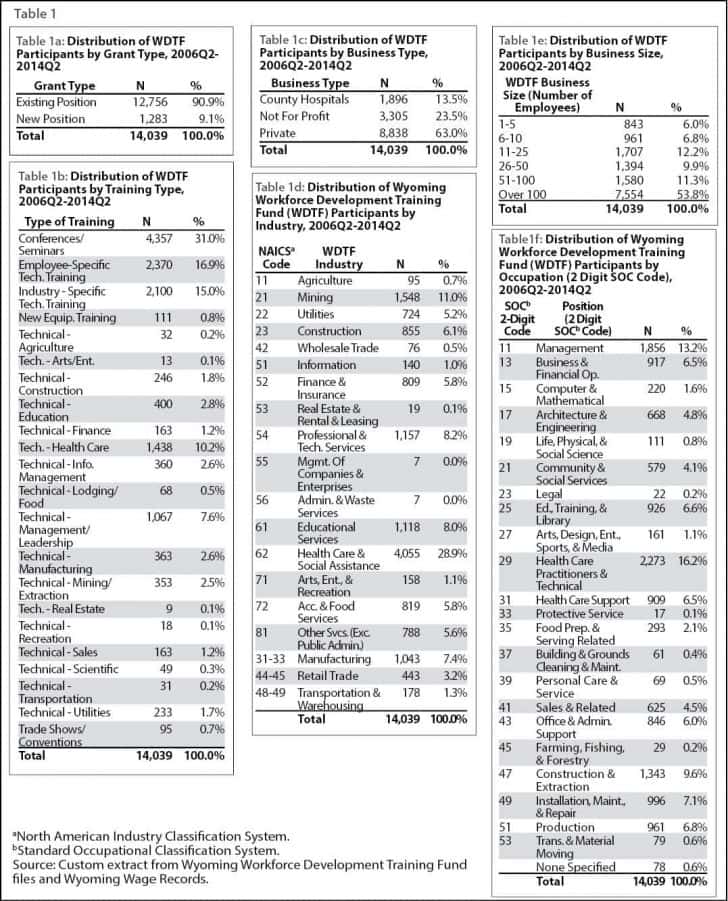
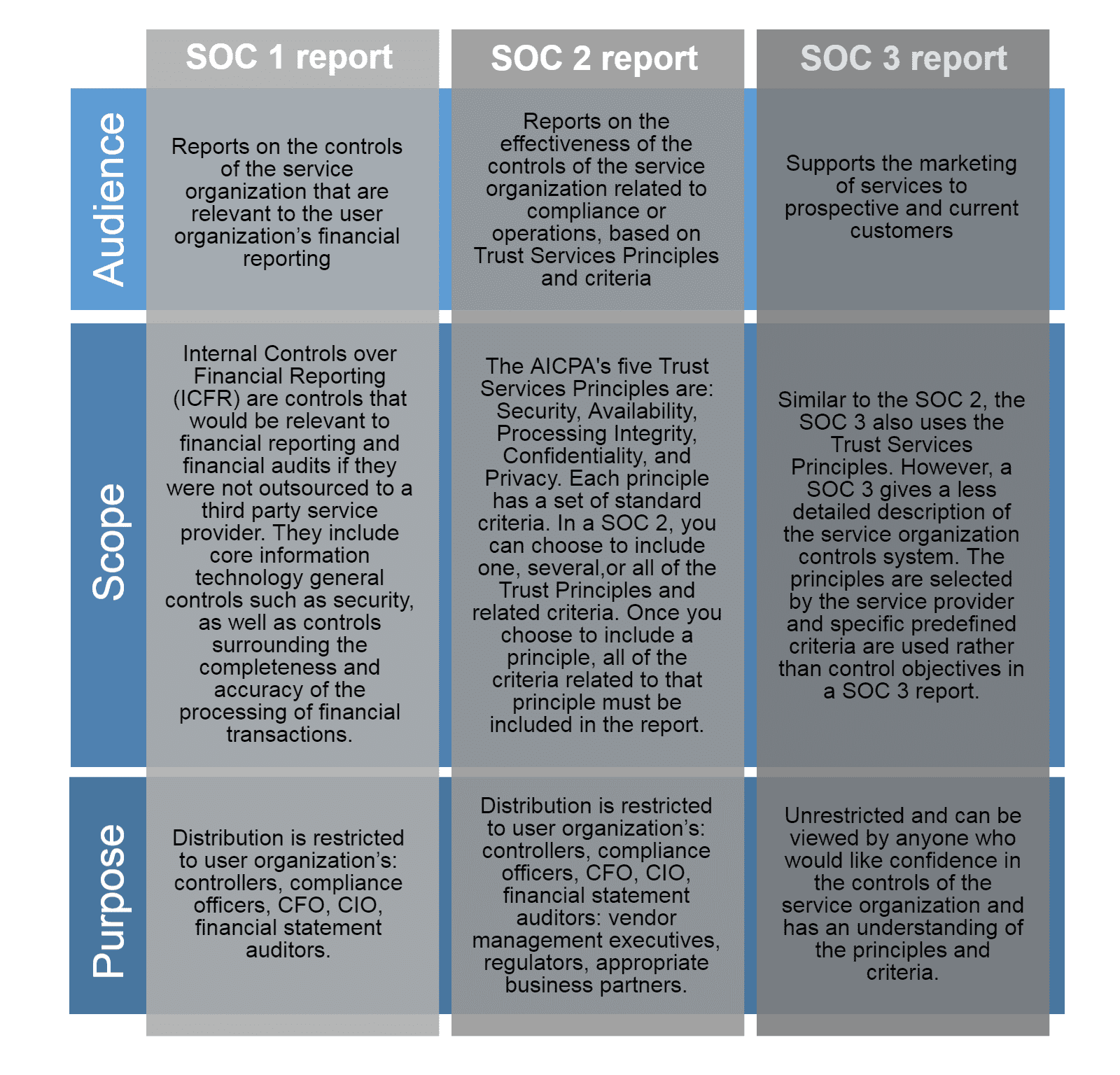
SOC stands for Service Organization Control. A SOC Report Example is a report that provides detailed information about a service organization’s controls that are relevant to security, availability, processing integrity, confidentiality, or privacy. These reports are prepared by independent auditors who assess the organization’s controls against specific criteria, such as the SOC 2 or SOC 3 criteria.
Why is a SOC Report Example Important?
Obtaining a SOC Report Example is important for service organizations because it helps build trust with their clients. It provides assurance that the organization has effective controls in place to protect sensitive information and ensures that the organization is in compliance with relevant regulatory requirements. SOC reports are also useful for organizations that outsource services to third-party providers, as they can use the reports to assess the security and reliability of those providers.
Types of SOC Reports
There are three types of SOC reports:
- SOC 1 Report
This report focuses on controls relevant to financial reporting, such as controls over financial statement accuracy and completeness. - SOC 2 Report
This report focuses on controls relevant to security, availability, processing integrity, confidentiality, or privacy. The SOC 2 report is divided into two types:a. Type I
This report describes the organization’s controls at a specific point in time.
SOC 1 Report Example And SOC 1 Report Definition b. Type II
This report describes the effectiveness of the organization’s controls over a period of time, typically 6-12 months. - SOC 3 Report
This report is similar to the SOC 2 report but is designed for a broader audience. It provides a summary of the organization’s controls and can be made available to the public.
Examples of SOC Reports
To help you understand how SOC reports work, here are a few examples of SOC reports:
- SOC 1 Type II Report for a payroll processing company: This report would detail the controls the company has in place to ensure accurate and complete payroll processing, such as validation of employee data and processing of tax withholdings.
- SOC 2 Type I Report for a cloud hosting provider: This report would detail the controls the provider has in place to ensure the security and availability of their hosting services, such as firewalls, intrusion detection systems, and disaster recovery procedures.
- SOC 3 Report for a medical billing company: This report would provide a summary of the company’s controls for security, processing integrity, confidentiality, and privacy, allowing potential clients to assess the company’s capabilities in those areas.
Conclusion
Obtaining a SOC Report Example is an important step for service organizations that want to build trust with their clients and demonstrate their commitment to data security. By understanding the different types of SOC reports available and reviewing examples of these reports, organizations can ensure that they have effective controls in place to protect sensitive information and comply with regulatory requirements.
It’s important to note that SOC reports are not one-size-fits-all. The scope and criteria for each report can vary depending on the organization’s services and the needs of their clients. It’s important for service organizations to work with their auditors to determine which SOC report is most appropriate for their needs.
In addition to building trust with clients and demonstrating compliance with regulatory requirements, SOC reports can also provide a competitive advantage for service organizations. By demonstrating that they have effective controls in place to protect sensitive information, organizations can differentiate themselves from their competitors and attract new clients.
Overall, obtaining a SOC Report Example is an important step for service organizations that want to demonstrate their commitment to data security and compliance with regulatory requirements. By understanding the different types of SOC reports available and reviewing examples of these reports, organizations can ensure that they have effective controls in place to protect sensitive information and build trust with their clients.