A Penetration Testing Sample Report is your road map to determine what the next step should be in regards to Penetration Testing. This can also be considered as a guideline regarding what steps are needed to be taken. If you wish to do it, then you will need to know which way you should go in order to achieve the best results possible.
These are the steps that you can take to be successful in any given situation and they will make up the core of the management entity that you wish to build. However, there are specific factors that will guide you through this process. The first step would be to know what the problems are. When you know what the problems are, you are in a better position to outline the problems.
Once you have identified the problems, you will then have a better understanding of how to solve them. Once you have done this, you will have a better understanding of how to go about your plan. However, just like anything else, there are three basic types of problems that can be identified.
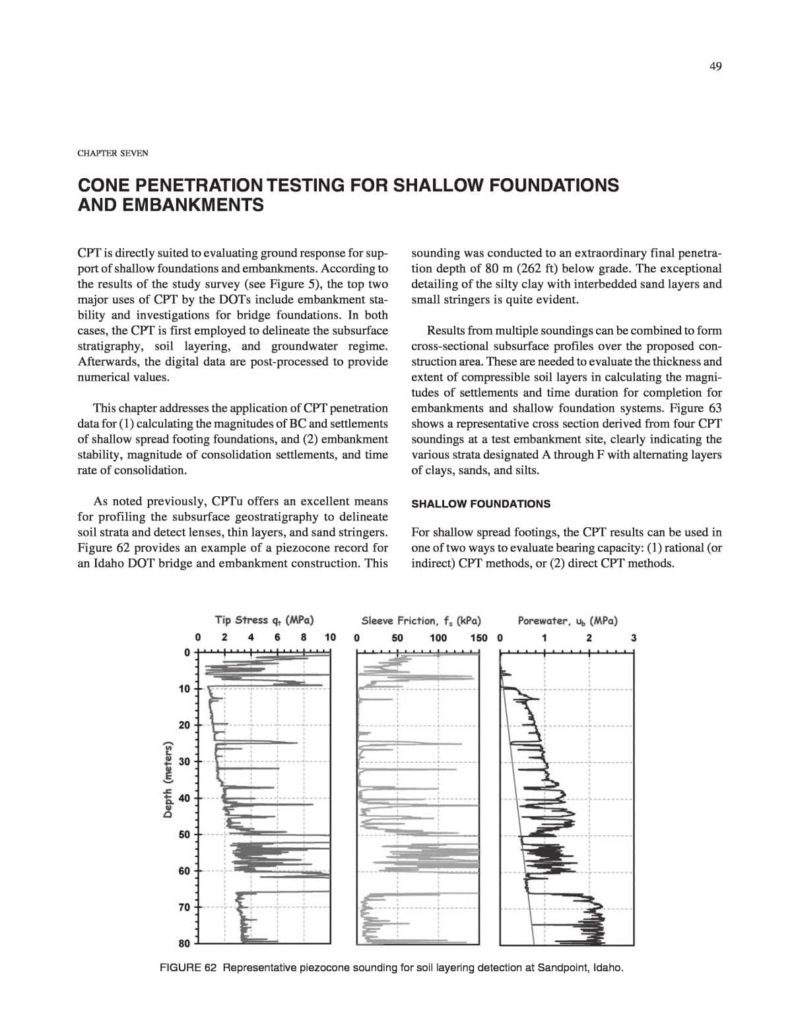
One of the main things that will need to be completed is the development of the database. This means that a new system has to be built to verify that the application works properly. For this reason, it will be necessary to obtain the database that was required for the initial test.
There will also be a need to have a full detail of the security in place. This will enable the testing to be completed in a matter of days without having to spend a great deal of time in gaining access to the actual database. However, the software that was used to develop the database will have to be identical for each of the teams that will be doing the test.
The next step is to show the development team at the highest level that there has been a breach. With all of the information that they need to know, it is important to be able to provide it to the management. With the software that was used to create the system, it should be easy to provide this proof.
The manual testing can be conducted manually. However, you will have to first of all identify the areas that need attention. From there, you can move on to write the procedures.
Finally, if you are going to perform Penetration Testing, then you will need to be able to test the system to the T. While it may be tempting to test every single area of the system, it is necessary to focus only on the parts that have a weak point. By targeting the weak spots, you will be sure to find it, and it will not be difficult to find.