How to Use an IT Security Incident Report Template
An IT security incident report template can help organizations quickly and effectively respond to security incidents. Learn how to use this tool to protect your business.
In today’s digital age, cyberattacks are becoming increasingly common and sophisticated. Cybercriminals are always on the lookout for vulnerabilities in systems and networks to exploit. That’s why it’s crucial for organizations to have robust IT security measures in place to safeguard their data and systems from these threats. However, even with the best security systems, incidents can still occur, and when they do, it’s important to respond quickly and effectively. This is where an IT security incident report template comes in handy.
What is an IT Security Incident Report Template?
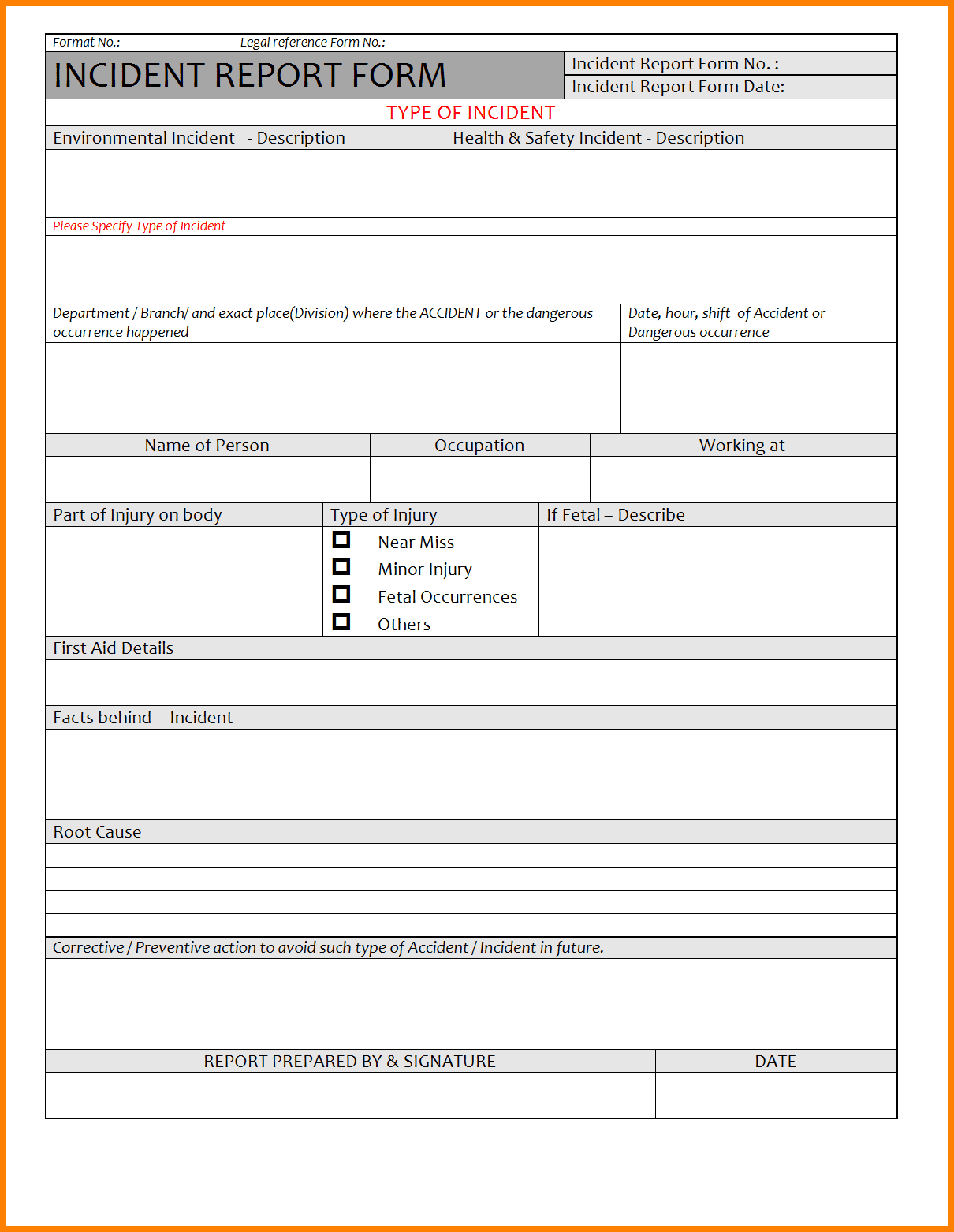
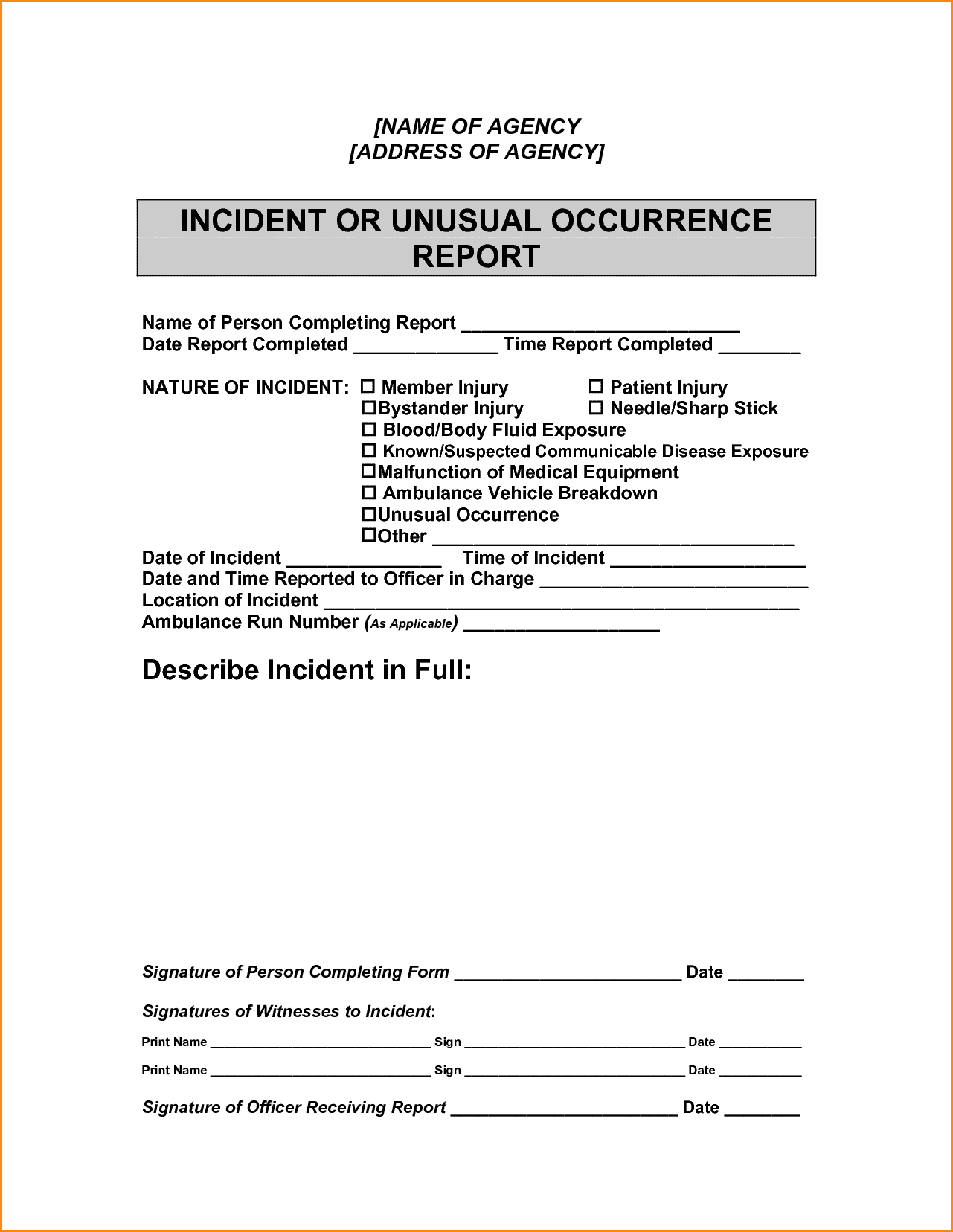
An IT security incident report template is a document that outlines the process for reporting and responding to security incidents in an organization. It typically includes sections for documenting the incident’s details, the affected systems, and the steps taken to contain and remediate the incident. Having a standardized template ensures that all incidents are reported and documented consistently, making it easier to track and analyze incidents and identify trends or patterns.
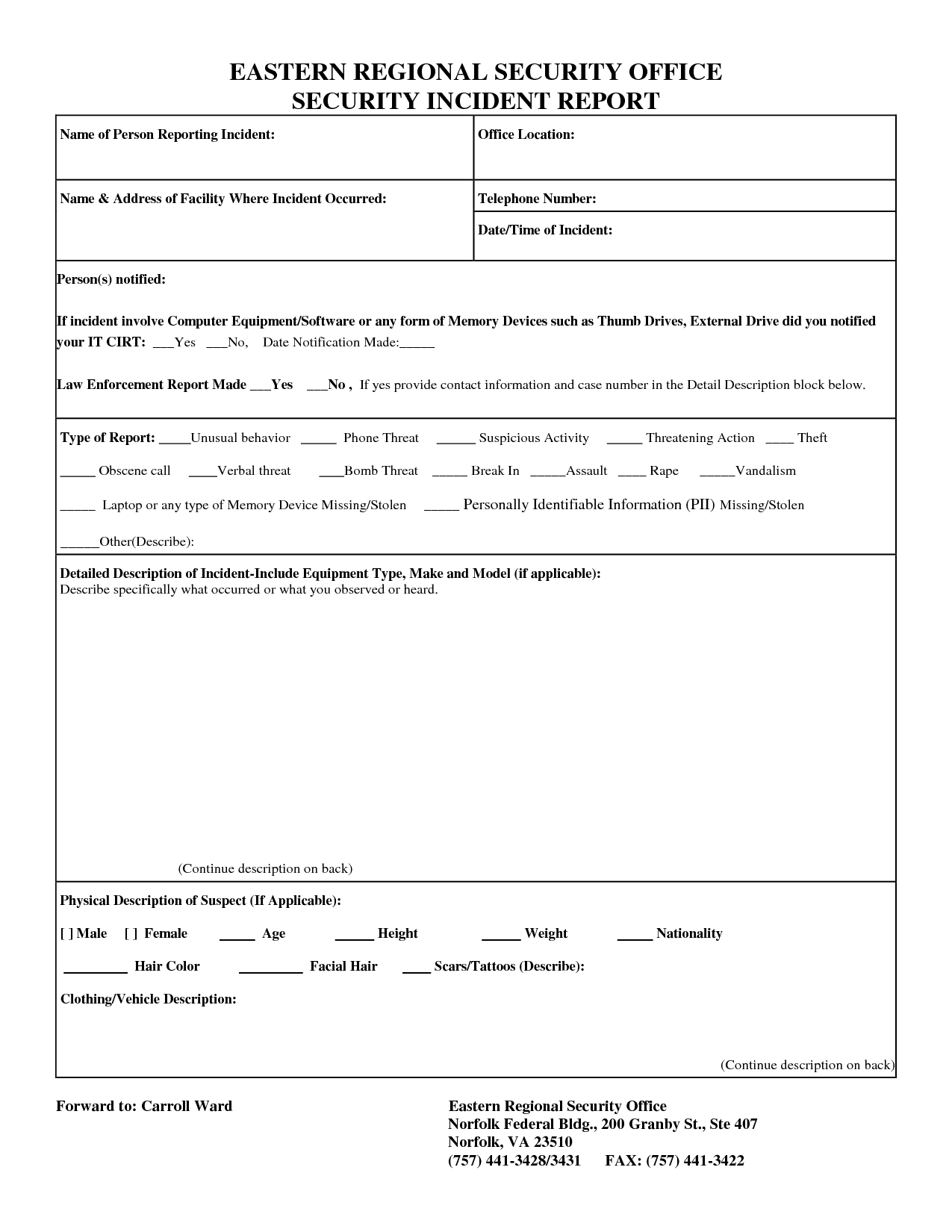
How to Use an IT Security Incident Report Template
Step 1: Identify the Incident
The first step in using an IT security incident report template is to identify the incident. This could be a security breach, a system outage, a malware infection, or any other event that could compromise the confidentiality, integrity, or availability of the organization’s data or systems. Once the incident is identified, it’s important to gather as much information about it as possible, such as the time and date of the incident, the affected systems or applications, and the nature of the incident.
Step 2: Document the Incident
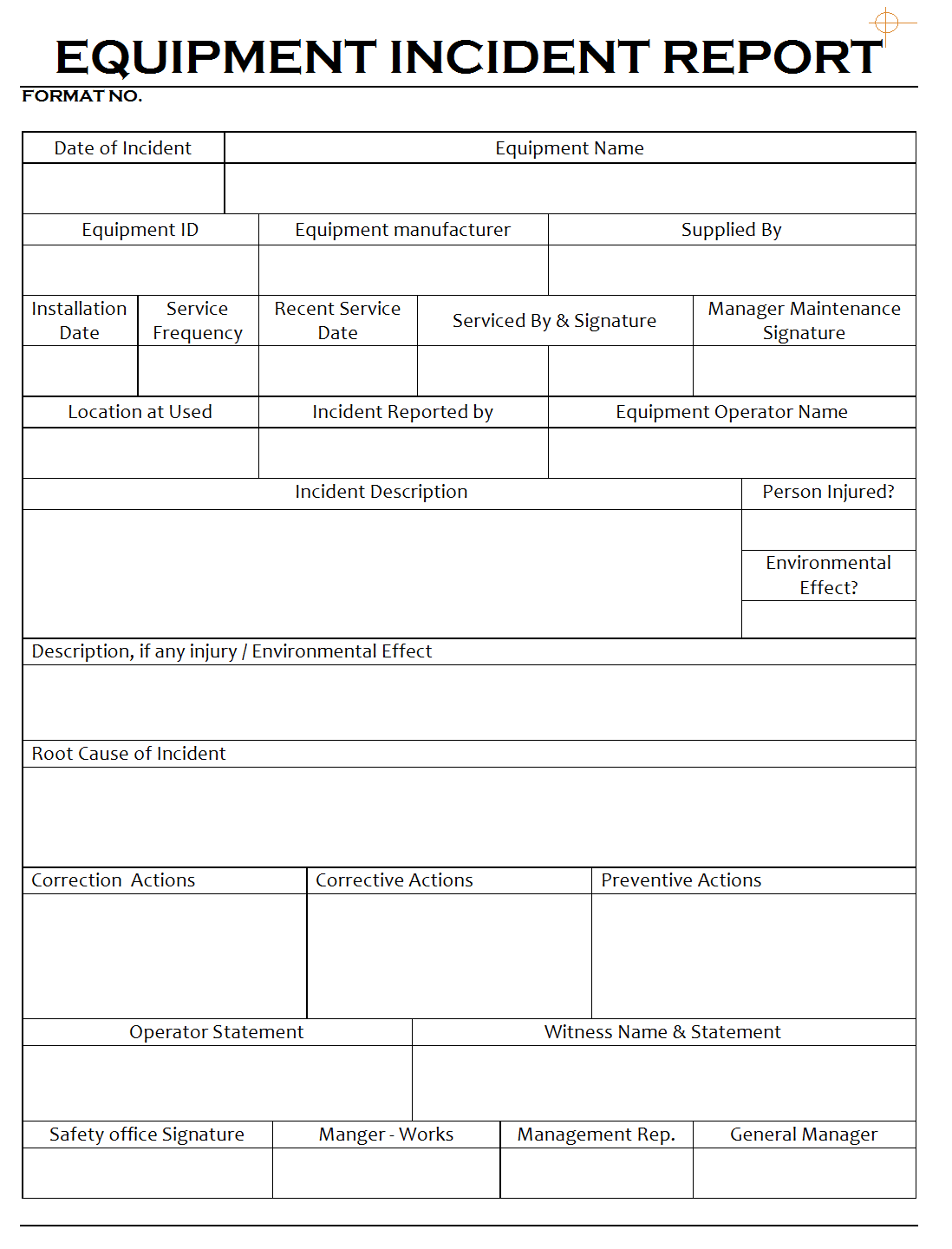
The next step is to document the incident using the IT security incident report template. The template should have fields for capturing all the necessary details about the incident, such as the type of incident, the date and time of the incident, the systems or applications affected, and the severity of the incident. It’s essential to be as detailed as possible when documenting the incident, as this information will be used later to analyze the incident and develop a response plan.
Step 3: Contain the Incident
Once the incident is documented, the next step is to contain it. This involves taking immediate action to stop the incident from spreading and causing further damage. Depending on the nature of the incident, containment measures could include isolating affected systems or applications, shutting down network connections, or disabling user accounts. It’s important to document all containment measures taken in the IT security incident report template.
Step 4: Investigate the Incident
After the incident is contained, the next step is to investigate it thoroughly. This involves analyzing the incident’s root cause, identifying any vulnerabilities or weaknesses in the organization’s systems or processes that contributed to the incident, and determining the extent of the damage. It’s crucial to document all investigative activities in the IT security incident report template, including the tools and techniques used to conduct the investigation.
Step 5: Remediate the Incident
Once the incident is investigated, the next step is to remediate it. This involves taking steps to repair the damage caused by the incident, such as restoring data from backups, patching vulnerabilities, or reconfiguring systems to prevent similar incidents from occurring in the future. It’s important to document all remediation measures taken in the IT security incident report template.
Step 6: Review and Improve
The final step in using an IT security incident report template is to review and improve the organization’s security incident response process. This involves analyzing the incident and the organization’s response to it, identifying any areas for improvement, and updating the template and the response process accordingly. It’s essential to conduct regular reviews and updates to ensure that the organization’s security incident response process remains effective and up-to-date.
Benefits of Using an IT Security Incident Report Template
Using an IT security incident report template offers several benefits to organizations. Firstly, it provides a standardized framework for responding to security incidents, ensuring that all incidents are reported and documented consistently. This makes it easier to track and analyze incidents, identify trends or patterns, and develop effective response strategies.
Secondly, using a template can save time and effort in responding to incidents. Rather than having to create a response plan from scratch every time an incident occurs, the organization can simply use the template as a starting point, customizing it as needed to fit the specific incident.
Finally, using an IT security incident report template can help organizations improve their security posture over time. By documenting and analyzing incidents and the organization’s response to them, the organization can identify weaknesses or vulnerabilities in their security systems and processes, and take steps to address them. This can help prevent similar incidents from occurring in the future and improve overall security.
Conclusion
In today’s digital age, cyberattacks are a significant threat to organizations of all sizes and industries. Having an effective IT security incident response process is crucial for protecting against these threats. Using an IT security incident report template can help organizations quickly and effectively respond to security incidents, ensuring that they are documented and analyzed consistently and that response strategies are developed and improved over time. By using this tool, organizations can better protect their data and systems and minimize the impact of security incidents on their operations and reputation.