In the dynamic landscape of cybersecurity, businesses are constantly challenged to fortify their defenses against an evolving array of threats. As organizations strive to safeguard their sensitive data and maintain operational resilience, the role of Security Operations Centers (SOCs) becomes increasingly pivotal. At the heart of an effective SOC lies the SOC 3 Report, a potent tool that exemplifies a commitment to robust security practices. In this article, we delve into the significance of SOC 3 Report Example and its profound implications for modern businesses.
Understanding SOC 3 Report Example
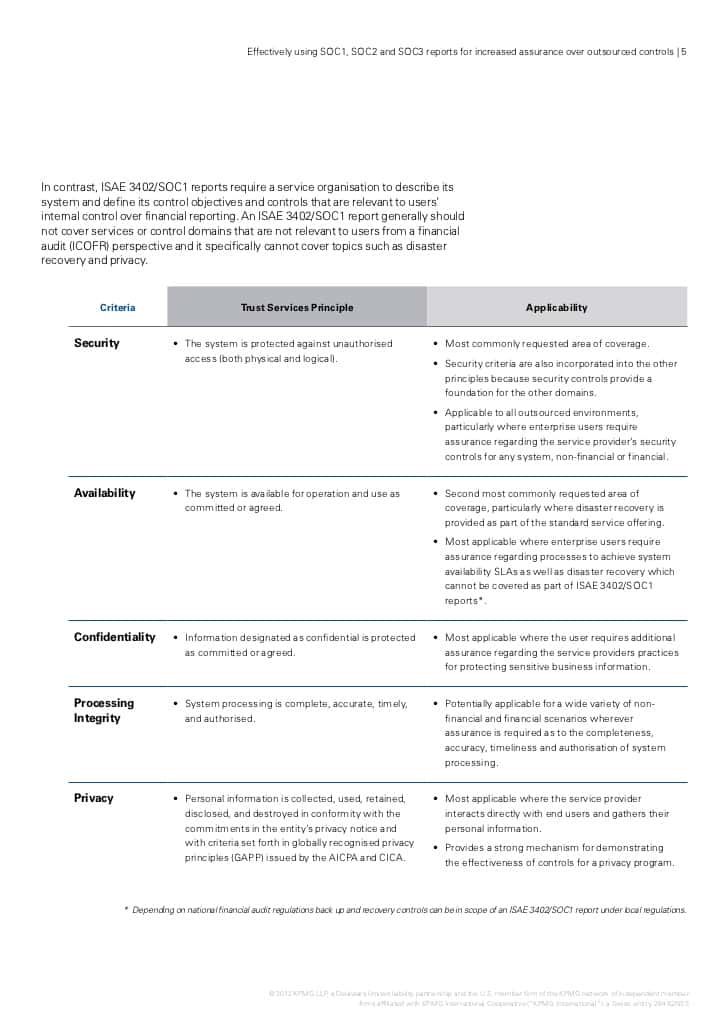
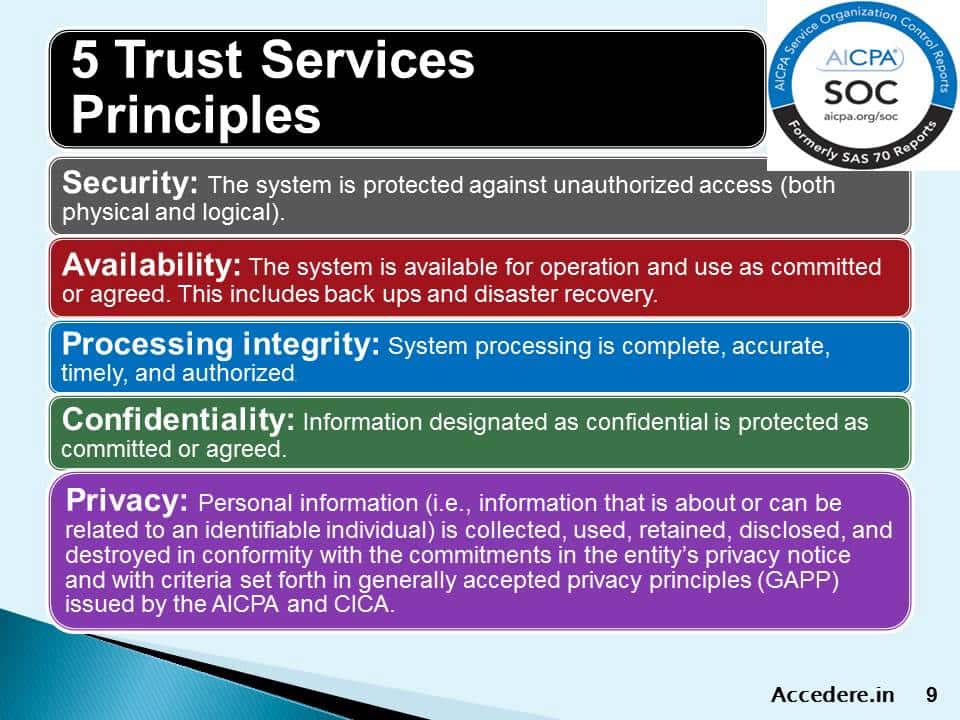
SOC 3 Report Example serves as a beacon of transparency and assurance for organizations seeking to instill trust among stakeholders. It encapsulates an independent auditor’s attestation of the effectiveness of an entity’s internal controls pertaining to security, availability, processing integrity, confidentiality, and privacy.
The Pillars of Security Reinforcement
- Comprehensive Assessment
SOC 3 Report Example provides a comprehensive assessment of an organization’s security posture, offering stakeholders valuable insights into the efficacy of its control environment. By scrutinizing critical areas such as data protection measures, access controls, and incident response protocols, businesses can identify vulnerabilities and implement remedial measures proactively. - Enhanced Credibility
In an era marred by data breaches and cybersecurity incidents, establishing credibility is paramount. SOC 3 Report Example serves as tangible evidence of an organization’s commitment to safeguarding sensitive information and adhering to stringent security standards. This, in turn, fosters trust among customers, partners, and regulatory bodies, bolstering the organization’s reputation in the marketplace. - Risk Mitigation
By conducting a thorough evaluation of internal controls and risk management practices, SOC 3 Report Example empowers organizations to mitigate potential threats effectively. By identifying and addressing vulnerabilities in real-time, businesses can preemptively thwart cyber-attacks and minimize the impact of security breaches, thereby safeguarding their operations and preserving business continuity.
Harnessing the Power of SOC 3 Report Example
- Strategic Decision Making
Armed with the insights gleaned from SOC 3 Report Example, organizations can make informed, strategic decisions pertaining to cybersecurity investments and resource allocation. By prioritizing areas identified as high-risk and optimizing security initiatives, businesses can maximize their defense capabilities and adapt to emerging threats with agility. - Regulatory Compliance
In an increasingly regulated landscape, compliance with industry-specific mandates and data protection regulations is non-negotiable. SOC 3 Report Example not only demonstrates adherence to regulatory requirements but also instills confidence in stakeholders regarding the organization’s commitment to data privacy and integrity. - Continuous Improvement
SOC 3 Report Example serves as a catalyst for continuous improvement, prompting organizations to refine and optimize their security practices iteratively. By leveraging the findings and recommendations outlined in the report, businesses can refine their control environment, implement best practices, and stay ahead of evolving threats in an ever-changing cybersecurity landscape.
The Evolution of Security Operations Centers
Over the years, Security Operations Centers (SOCs) have evolved from traditional perimeter defense models to sophisticated hubs of proactive threat detection and incident response. In this digital age where cyber threats lurk around every corner, SOCs play a pivotal role in safeguarding organizations against a myriad of adversaries ranging from opportunistic hackers to nation-state actors.

Real-Time Threat Monitoring
Central to the functionality of modern SOCs is real-time threat monitoring. Through the deployment of advanced security analytics tools and threat intelligence feeds, SOC analysts can scrutinize network traffic, endpoint activities, and system logs to identify anomalous behavior indicative of potential security breaches. By leveraging machine learning algorithms and behavioral analytics, SOCs can differentiate between benign anomalies and malicious activities, enabling swift and targeted response measures.
Incident Response and Containment
In the event of a security incident, SOC teams spring into action, orchestrating a coordinated response to contain the threat and mitigate its impact. From isolating compromised systems to initiating forensic investigations, SOC analysts work tirelessly to restore the integrity of the organization’s infrastructure and minimize downtime. By adhering to predefined incident response procedures and leveraging automation where possible, SOCs can expedite the resolution process and minimize the fallout from security breaches.
Threat Intelligence Integration
To stay ahead of the curve in the ever-evolving threat landscape, SOCs integrate threat intelligence into their operations, enabling them to anticipate emerging threats and proactively fortify their defenses. By leveraging feeds from reputable threat intelligence providers and collaborating with industry peers, SOCs can augment their understanding of adversary tactics, techniques, and procedures (TTPs), empowering them to preemptively thwart cyber-attacks before they materialize.

Continuous Improvement and Adaptation
The efficacy of a SOC hinges upon its ability to adapt to evolving threats and technological advancements. Through continuous monitoring, analysis, and refinement of security processes, SOCs can stay abreast of emerging threats and adapt their defense strategies accordingly. By fostering a culture of collaboration, innovation, and knowledge sharing, organizations can empower their SOC teams to evolve in lockstep with the ever-changing cybersecurity landscape.
The Human Element
Amidst the proliferation of advanced technologies and automation, the human element remains indispensable to the success of SOCs. Skilled analysts armed with domain expertise and critical thinking capabilities serve as the frontline defenders, tirelessly safeguarding organizations against cyber threats. By investing in employee training, mentorship programs, and professional development initiatives, organizations can nurture a cadre of elite SOC professionals capable of thwarting even the most sophisticated adversaries.
Conclusion
In an era defined by digital transformation and ubiquitous cyber threats, Security Operations Centers (SOCs) serve as the linchpin of modern cybersecurity strategies. From real-time threat monitoring to proactive incident response, SOCs play a pivotal role in safeguarding organizations against a myriad of adversaries. By embracing the principles of agility, collaboration, and continuous improvement, organizations can empower their SOC teams to adapt and thrive in the face of evolving threats, ensuring the resilience and integrity of their digital infrastructure.