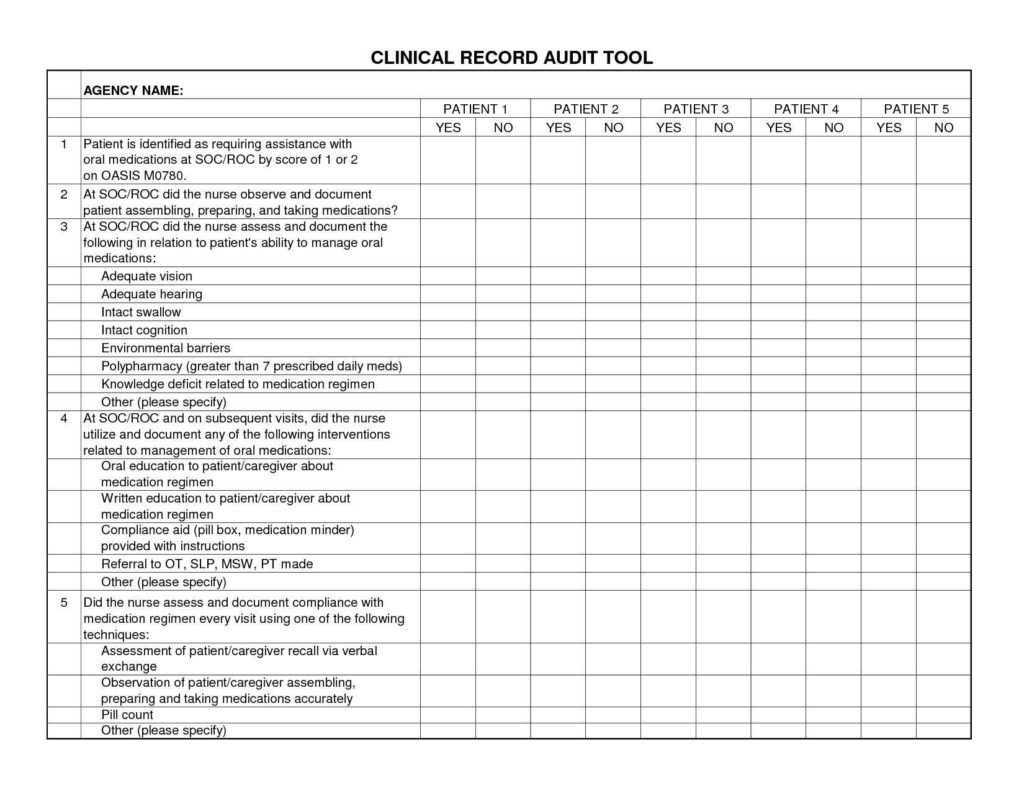
Get an in-depth understanding of SOC 2 Report Sample in this comprehensive guide. Learn about its purpose, contents, and importance for businesses.
As cyber threats become more sophisticated and prevalent, businesses are increasingly taking measures to protect their systems and data. One such measure is SOC 2 compliance, which ensures that a business’s systems and processes meet the highest standards of security and privacy.
A SOC 2 report is a crucial component of SOC 2 compliance, and it provides an assessment of a company’s security controls. In this article, we will discuss SOC 2 Report Sample, including its purpose, contents, and importance.
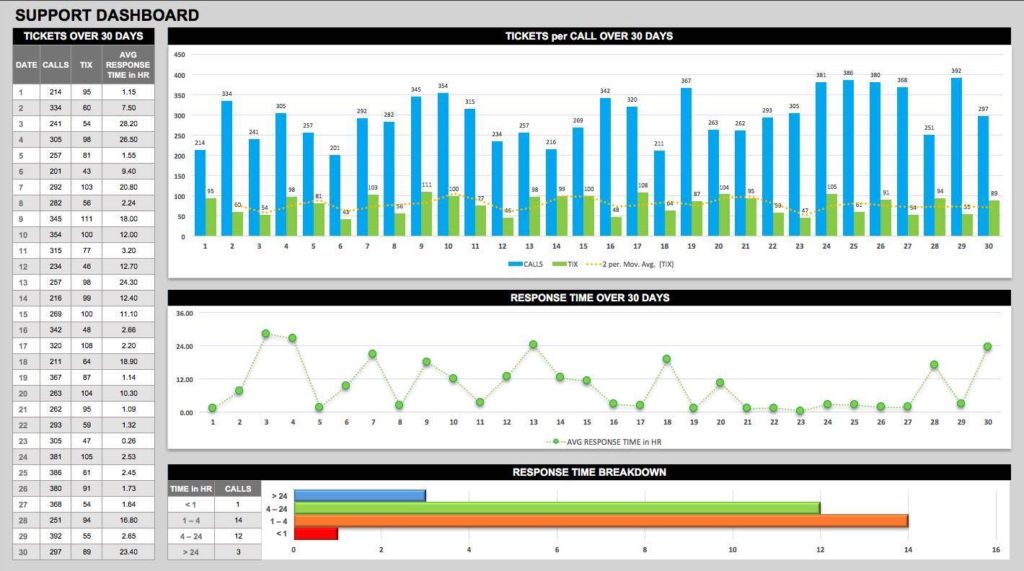
What is a SOC 2 Report?
A SOC 2 report is an independent audit report that attests to the effectiveness of a company’s controls related to security, availability, processing integrity, confidentiality, and privacy. It is based on the AICPA’s Trust Services Criteria and is designed to help organizations evaluate their security posture and provide assurance to their customers.
A SOC 2 report can be either a Type 1 or a Type 2 report. A Type 1 report provides an assessment of a company’s controls at a specific point in time, while a Type 2 report provides an assessment of a company’s controls over a period of time (typically six months to a year).
Purpose of a SOC 2 Report Sample
The purpose of a SOC 2 report sample is to provide a template for organizations to use when preparing their own SOC 2 reports. It contains sample language and formatting that can be used as a guide when drafting a report.

Contents of a SOC 2 Report Sample
A SOC 2 report typically includes the following sections:
- Management’s Assertion
This section is a statement from management that the company’s controls meet the AICPA’s Trust Services Criteria. - Service Auditor’s Opinion
This section is a statement from the service auditor that the company’s controls have been evaluated in accordance with the AICPA’s Trust Services Criteria. - Description of the System
This section provides a high-level overview of the system being audited, including its objectives and key components. - Control Environment
This section describes the company’s overall control environment, including its policies, procedures, and governance. - Risk Assessment
This section describes how the company identifies and assesses risks to its system. - Control Activities
This section describes the specific controls that the company has in place to mitigate identified risks. - Monitoring Activities
This section describes how the company monitors its controls to ensure their ongoing effectiveness.
Importance of a SOC 2 Report
A SOC 2 report is important for several reasons:
- Compliance
SOC 2 compliance is increasingly becoming a requirement for businesses that provide services to other companies. A SOC 2 report provides assurance to customers that their data is being handled securely and confidentially. - Competitive Advantage
A SOC 2 report can provide a competitive advantage for a company, as it demonstrates a commitment to security and privacy. - Risk Management
A SOC 2 report can help a company identify and mitigate risks to its systems and data.
Tips for Preparing for a SOC 2 Audit
Preparing for a SOC 2 audit can be a daunting task, but there are several steps that organizations can take to ensure a successful outcome. Here are some tips for preparing for a SOC 2 audit:
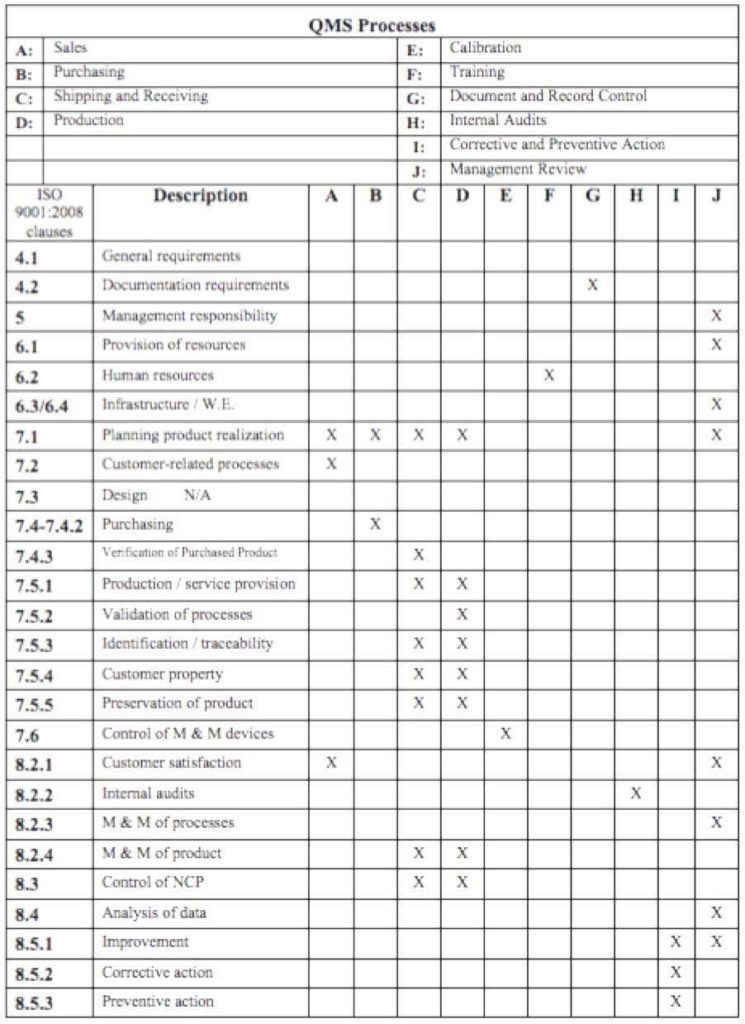
- Identify the Scope
Before starting the audit, it is important to clearly define the scope of the audit. This includes identifying the systems and processes that will be audited, as well as the controls that will be evaluated. - Gather Documentation
The auditor will require documentation to support the company’s controls, so it is important to gather all relevant documentation in advance of the audit. This includes policies, procedures, and evidence of controls. - Conduct a Risk Assessment
A risk assessment should be conducted to identify potential risks to the system and to prioritize controls to mitigate those risks. - Perform a Gap Analysis
A gap analysis should be conducted to identify any gaps in the company’s controls and to develop a plan to address those gaps. - Train Staff
Staff should be trained on the company’s policies and procedures to ensure that they are aware of their responsibilities and understand the importance of security and privacy.
Conclusion
A SOC 2 report sample provides a valuable resource for organizations preparing for a SOC 2 audit. By understanding the purpose, contents, and importance of a SOC 2 report, organizations can take steps to ensure a successful audit and demonstrate their commitment to security and privacy. By following the tips outlined in this article, organizations can prepare for a SOC 2 audit with confidence and achieve SOC 2 compliance.