In the ever-evolving digital landscape, ensuring the security and privacy of sensitive information has become paramount. Organizations handling customer data are expected to adhere to stringent standards to guarantee the safety of this data. One such critical standard is SOC 2 compliance. In this comprehensive guide, we will explore the intricacies of SOC 2 through a real-world lens with our SOC 2 Report Example.
Understanding SOC 2 Compliance
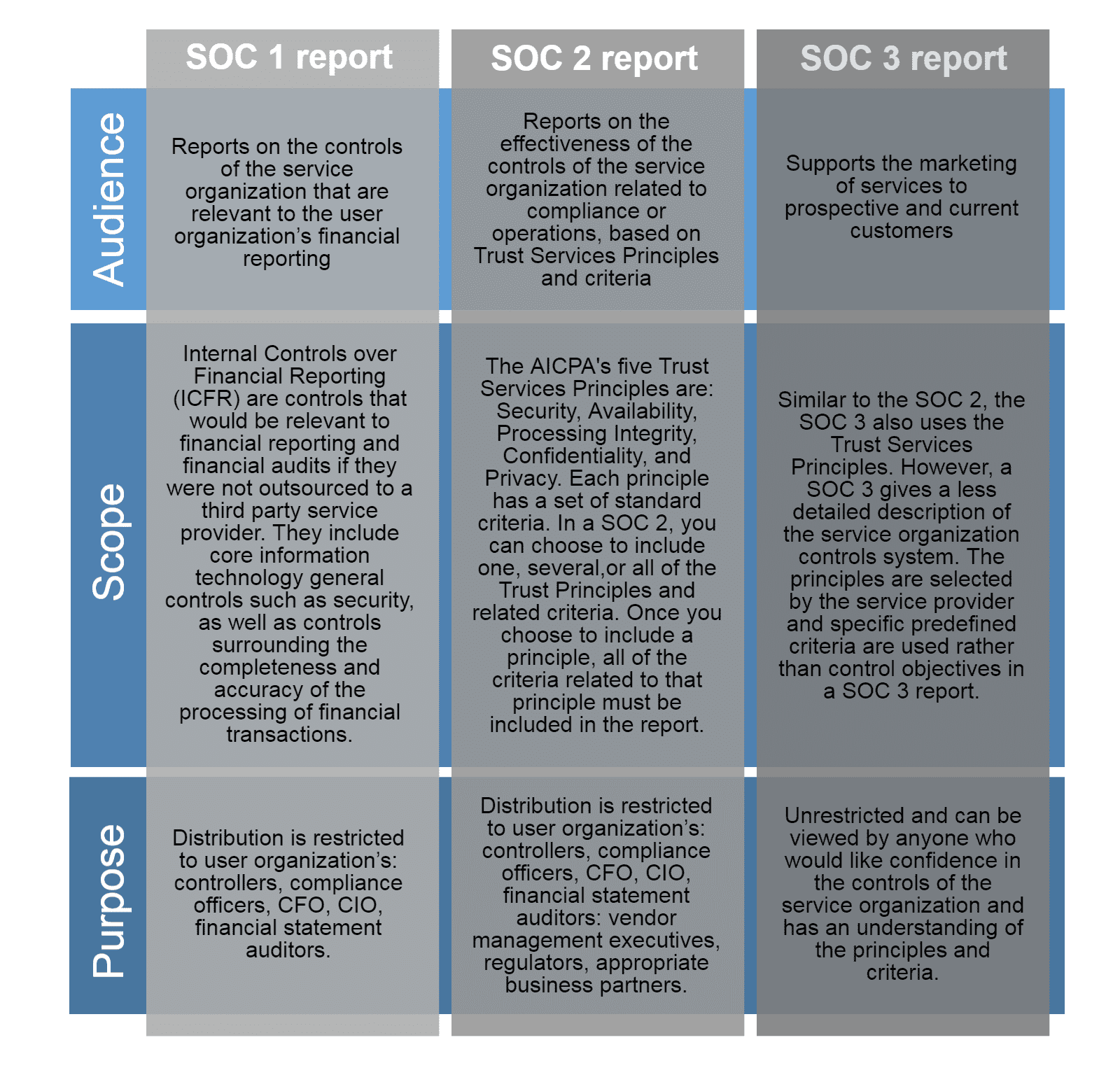
SOC 2, short for Service Organization Control 2, is a framework designed by the American Institute of CPAs (AICPA) to manage and secure customer data. It focuses on five crucial trust service criteria: security, availability, processing integrity, confidentiality, and privacy. Achieving SOC 2 compliance ensures that an organization’s systems and processes meet the highest standards of security and reliability.
Navigating the SOC 2 Report
1. Security – The Fortification of Digital Perimeters
The SOC 2 Report Example takes us into the realm of security, showcasing how organizations establish and maintain a robust defense against unauthorized access. Encryption protocols, access controls, and incident response mechanisms are laid bare, emphasizing the commitment to safeguarding information.

2. Availability – Ensuring Seamless Operations
Explore how businesses guarantee uninterrupted service with insights into their infrastructure, redundancies, and disaster recovery plans. The SOC 2 Report Example illustrates the meticulous planning behind maintaining high availability and minimizing downtime.
3. Processing Integrity – The Backbone of Reliable Operations
Dive into the processes that uphold the accuracy and completeness of data. The report demonstrates how organizations ensure that their systems operate reliably to meet business objectives and prevent data manipulation.
4. Confidentiality – Safeguarding Sensitive Information
Discover the measures in place to protect sensitive data from unauthorized access. The SOC 2 Report Example lays out the protocols and controls implemented to maintain the confidentiality of information, earning the trust of customers and partners.
5. Privacy – Respecting and Protecting Personal Information
In an era of heightened privacy concerns, understanding how organizations handle personal information is crucial. The SOC 2 Report Example walks you through the policies and practices employed to respect and protect individuals’ privacy.
Real-world Application
The SOC 2 Report Example isn’t just a theoretical document; it reflects the commitment of organizations to meet and exceed industry standards. By examining a tangible example, businesses gain insights into best practices, helping them align their operations with the highest standards of security and reliability.
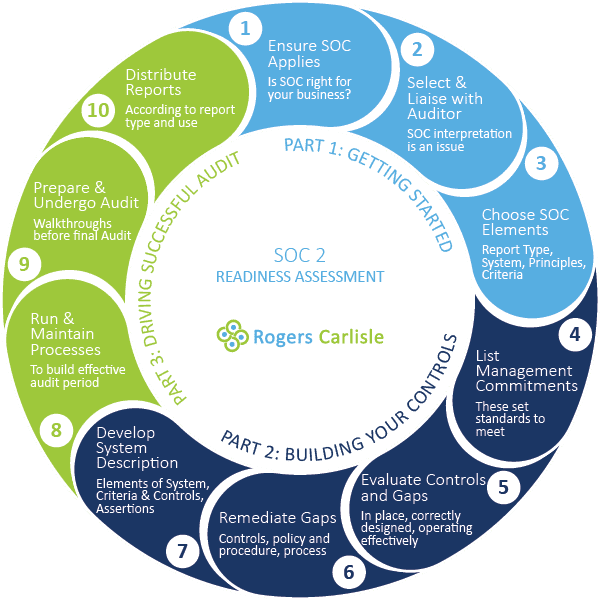
The Road to SOC 2 Compliance
Embarking on the journey towards SOC 2 compliance is a strategic decision that requires meticulous planning and dedication. The SOC 2 Report Example sheds light on the steps organizations take to meet these stringent criteria. Let’s delve deeper into the key aspects that pave the way for a successful SOC 2 compliance journey.
1. Risk Assessment – Identifying and Mitigating Potential Threats
The SOC 2 Report Example outlines the risk assessment processes implemented by organizations. From identifying potential vulnerabilities to developing robust risk mitigation strategies, this section provides a roadmap for businesses to proactively address security challenges.
2. Policy and Procedure Documentation – The Foundation of Compliance
Understanding how organizations document their policies and procedures is crucial for establishing a strong compliance foundation. The SOC 2 Report Example showcases the clarity and precision required in articulating these guidelines to ensure seamless adherence to SOC 2 criteria.
3. Incident Response Planning – Navigating the Unexpected
Unforeseen incidents can occur, and it’s essential to have a well-defined incident response plan in place. The SOC 2 Report Example walks you through how organizations prepare for and respond to security incidents, minimizing potential damage and ensuring a swift resolution.
4. Continuous Monitoring and Improvement – A Dynamic Approach to Compliance
Achieving SOC 2 compliance is not a one-time effort but an ongoing commitment. The SOC 2 Report Example highlights how organizations implement continuous monitoring processes, ensuring that security measures remain effective and adapting to evolving threats in real-time.
Leveraging SOC 2 for Business Growth
Beyond being a mere regulatory requirement, SOC 2 compliance can be a strategic asset for business growth. The SOC 2 Report Example illuminates how organizations use their commitment to security and reliability as a competitive advantage. Customers and partners, armed with the knowledge of a company’s SOC 2 compliance, gain confidence in its ability to safeguard their data.
Tips for SOC 2 Success
- Start Early
Begin the compliance journey well in advance to allow for thorough preparation and implementation of necessary controls. - Engage Stakeholders
Foster a collaborative approach by involving key stakeholders throughout the process. Their insights and commitment are invaluable. - Regular Audits
Conduct regular internal audits to identify and address potential compliance gaps proactively. - Stay Informed
Keep abreast of evolving security threats and industry best practices to ensure that your organization’s controls remain effective.
Conclusion: A Blueprint for Security and Trust
The SOC 2 Report Example is not just a compliance document but a blueprint for creating a secure, trustworthy, and resilient organizational framework. By embracing SOC 2 principles, businesses can build a foundation that not only meets regulatory requirements but also instills confidence among clients and partners.
In an era where data integrity and security are paramount, SOC 2 compliance isn’t merely a checkbox; it’s a commitment to excellence. Explore our SOC 2 Report Example to navigate the path towards a secure, compliant, and thriving digital future. Trust in transparency, and let SOC 2 be the beacon guiding your organization to new heights of success.





