The Ultimate Guide to Writing a Computer Security Incident Report Template
Protect your business from cyber threats by learning how to write a comprehensive and effective computer security incident report template. Our guide will provide you with all the information you need to create a report that can help you mitigate future incidents.
As businesses rely more on technology, the threat of cyber-attacks and data breaches continues to increase. To protect your organization from such threats, it is crucial to have a computer security incident report template in place. In this article, we will provide you with a step-by-step guide on how to create a comprehensive and effective report that can help you manage future incidents.
What is a Computer Security Incident Report Template?
A computer security incident report template is a document that outlines the procedures and steps to be taken in the event of a security breach or incident. It provides a systematic approach to handling incidents, ensuring that all necessary actions are taken promptly and effectively. The report should include all details about the incident, including the type of attack, the affected systems, and the steps taken to mitigate the damage.
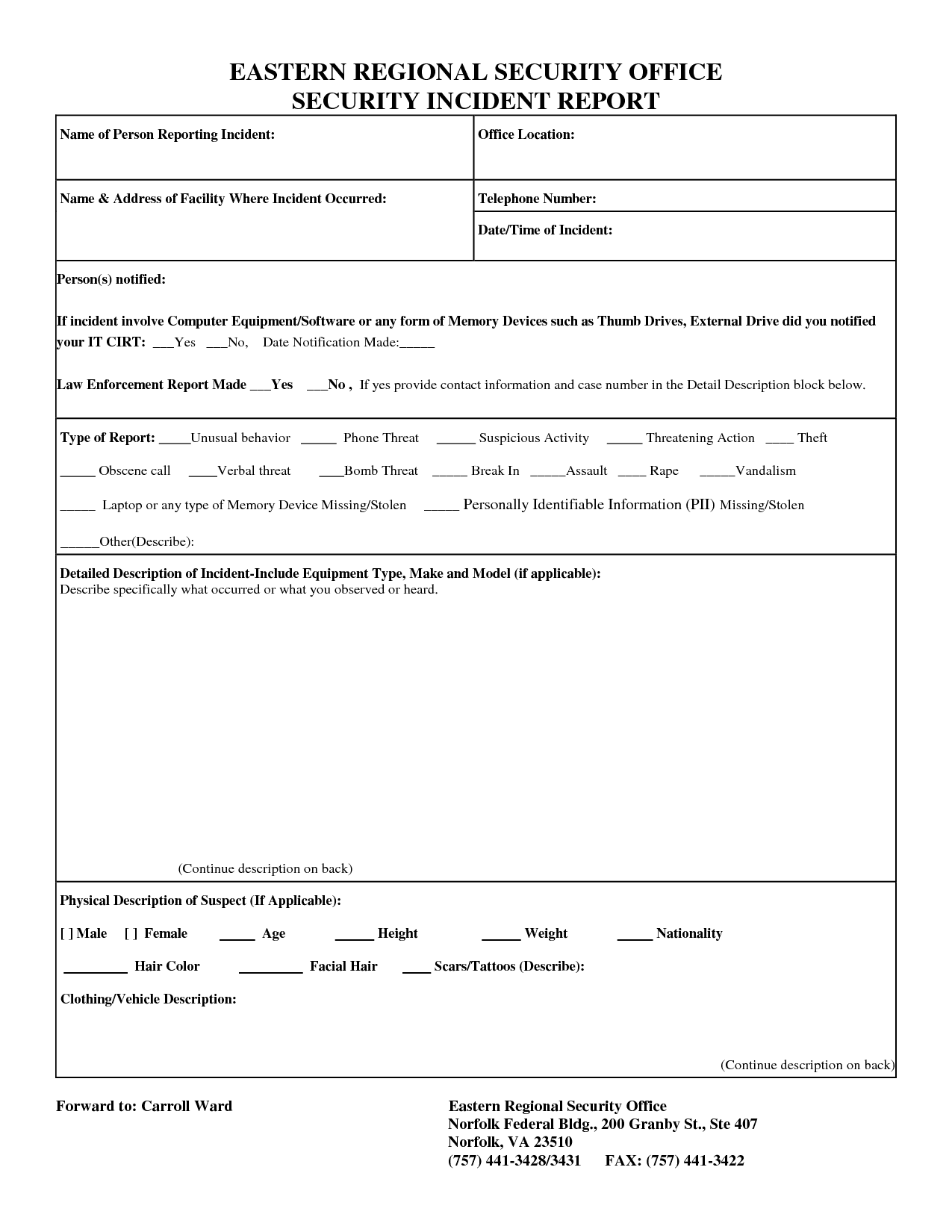
Why Do You Need a Computer Security Incident Report Template?
Having a computer security incident report template in place can help you mitigate the impact of a security breach. It provides a structured approach to managing incidents, ensuring that all necessary steps are taken promptly and efficiently. Additionally, it helps to improve response times and reduce the risk of data loss or theft. A well-written report can also help to identify the root cause of the incident, allowing you to take proactive steps to prevent future occurrences.
Creating a Computer Security Incident Report Template
Step 1: Determine the Scope of the Report
The first step in creating a computer security incident report template is to determine the scope of the report. This includes identifying the type of incident, the affected systems, and the stakeholders involved. You should also define the severity of the incident, as this will determine the level of response required.

Step 2: Gather Information
The next step is to gather all relevant information about the incident. This includes the date and time of the incident, the type of attack, and the affected systems. You should also gather information about the impact of the incident, such as data loss or theft. It is essential to document all details about the incident, as this will help to identify the root cause and prevent future incidents.
Step 3: Assess the Incident
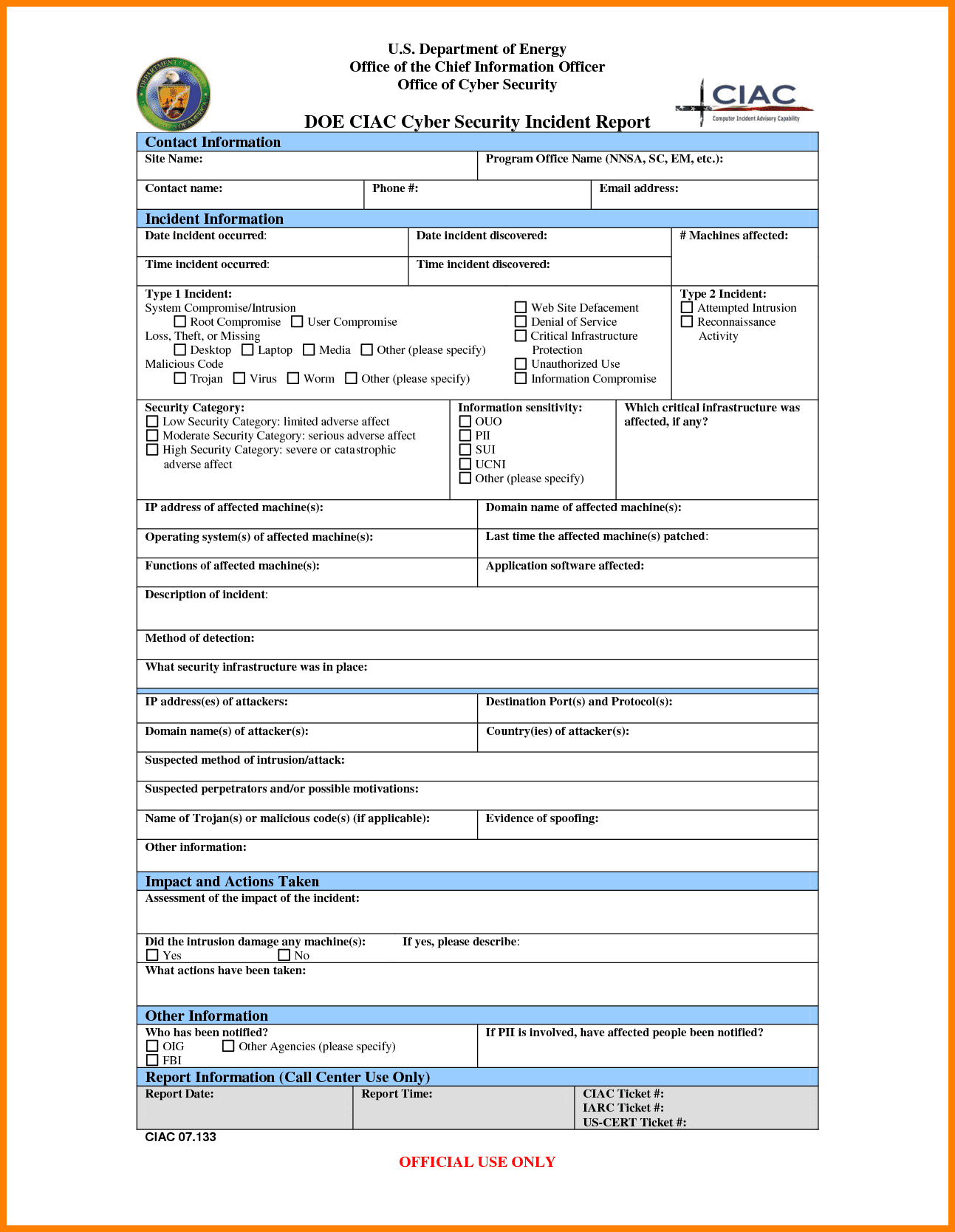
Once you have gathered all relevant information, the next step is to assess the incident. This includes determining the severity of the incident and identifying the potential impact on your organization. You should also assess the effectiveness of your current security measures and identify any gaps that need to be addressed.
Step 4: Develop an Action Plan
Based on your assessment, you should develop an action plan that outlines the steps to be taken to mitigate the damage and prevent future incidents. This may include patching vulnerabilities, updating security software, or implementing new security measures. Your action plan should also identify the responsible parties and define their roles and responsibilities.
Step 5: Communicate the Incident
The final step is to communicate the incident to all relevant stakeholders. This includes senior management, IT staff, and affected users. You should provide a summary of the incident, the steps taken to mitigate the damage, and any future action required. It is also essential to communicate the incident to law enforcement agencies if necessary.
Additional Tips for Writing a Computer Security Incident Report Template
To ensure that your report is effective and comprehensive, here are some additional tips to consider:
- Include all relevant details: Your report should include all details about the incident, including the type of attack, the affected systems, and the steps taken to mitigate the damage. The more information you include, the easier it will be to identify the root cause and prevent future incidents.
- Use clear and concise language: Your report should be easy to understand and free of technical jargon. Use clear and concise language to ensure that your message is conveyed effectively.
- Define roles and responsibilities: Your report should clearly define the roles and responsibilities of all parties involved. This includes the responsible parties for implementing security measures and for communicating the incident to stakeholders.
- Test your report: Once you have created your report, it is important to test it to ensure that it is effective. You can do this by running simulations or tabletop exercises to identify any gaps or weaknesses in your incident response plan.
Conclusion
Writing a computer security incident report template can be a challenging task, but it is an essential tool for protecting your business from cyber threats. By following the steps outlined in this guide and considering the additional tips provided, you can create a comprehensive and effective report that can help you mitigate future incidents and protect your organization from cyber-attacks. Remember to regularly review and update your report to ensure that it remains relevant and effective in today’s ever-changing threat landscape.